Lab 2.2: Port Scanning 2
Summary:
During this lab we worked more with nmap and port scanning. This time we used nmap against our windows machines and their rdp ports (3389). This lab was relativly straight forward I didn’t run into any big issues except for the terminal in kali being strange.
Edit: I went back to fix an error in 9 and figured out I had used a hot key to remove the border of the terminal…
Deliverable 1. Observe and repeat the following interaction between kali and your win10 system (substitute your IP addresses). Provide screenshot(s) similar to the one below that show:
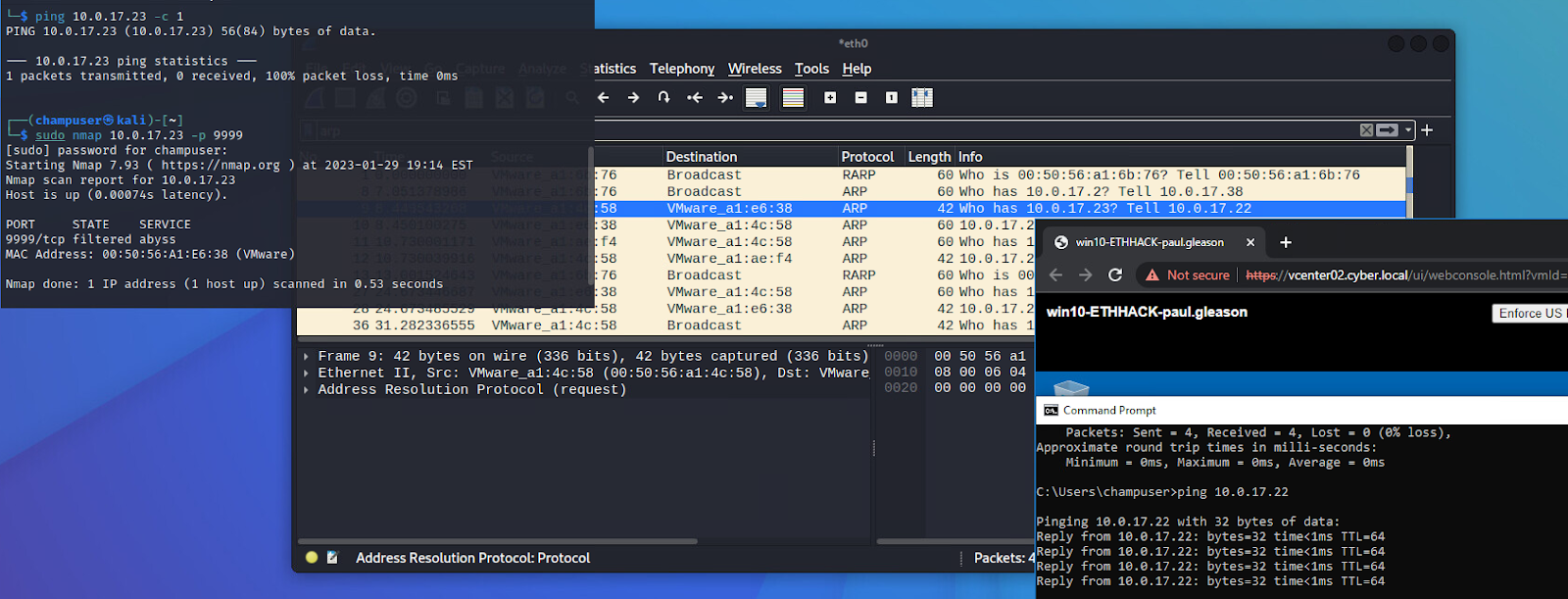
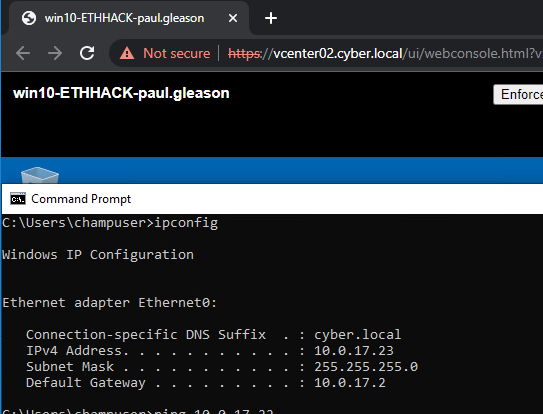
Deliverable 2. Figure out how to enable Remote Desktop Services on your windows 10 system using powershell or the command prompt and conduct an nmap scan against the rdp tcp port from your kali system.
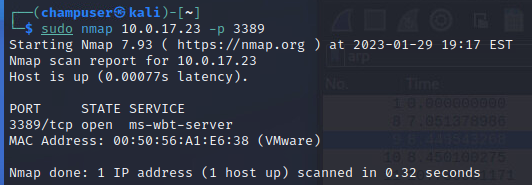
nmap command:
sudo nmap 10.0.17.23 -p 3389Deliverable 3. On Kali, make sure remmina is installed and figure out how to initiate an RDP session to your windows box. Provide a screenshot similar to the one below.
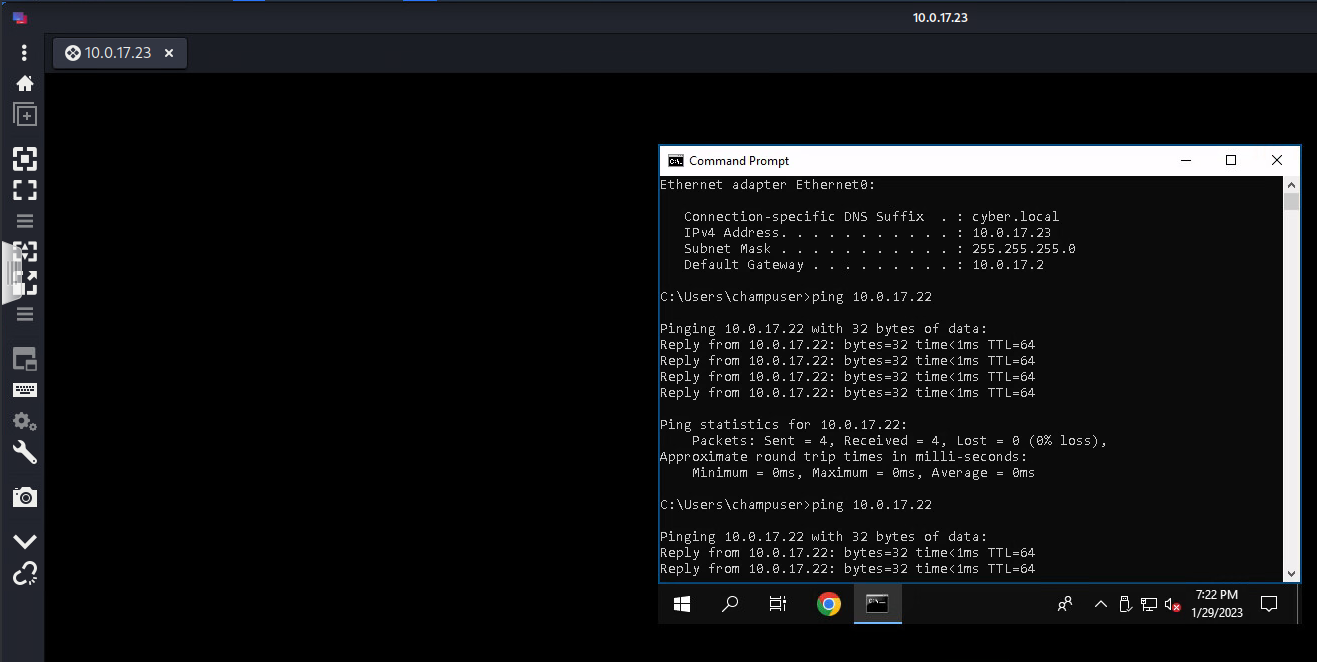
sudo apt install remminaDeliverable 4. Add the -sV flag to your previous nmap scan against rdp on windows 10 and provide a screenshot similar to the one below (include your nmap command). You will note a bit more verbiage than seen without the flag.
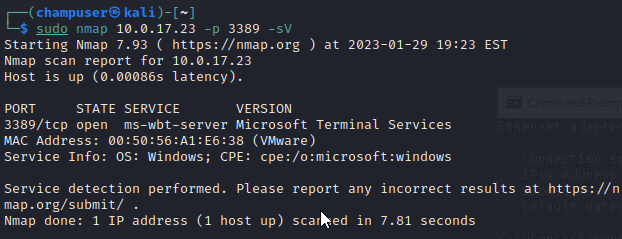
nmap command:
sudo nmap 10.0.17.23 -p 3389 -sVDeliverable 5. Replace -sV with -A to attempt to derive more information on the host and exposed service. Provide a screenshot similar to the one below. You will notice that the rdp-ntlm-info script provides a good deal of information (1) and that the OS detection output is not very accurate at all.
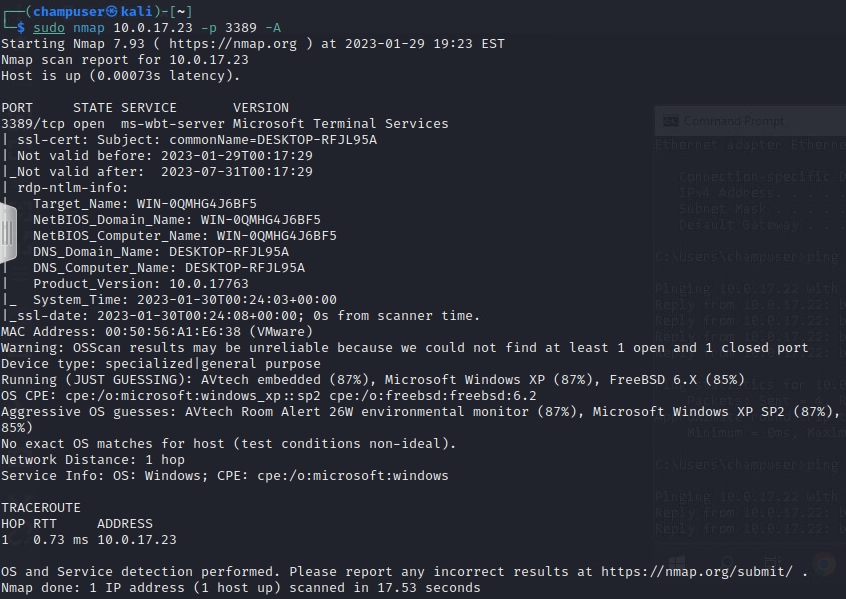
nmap command:
sudo nmap 10.0.17.23 -p 3389 -ADeliverable 6. Run an nmap scan against your windows 10 system. Only target tcp ports 1-6000. Provide a screenshot showing your command and output.
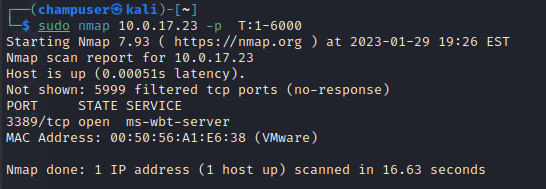
nmap command:
sudo nmap 10.0.17.23 -p T:1-6000Deliverable 7, Rescan ports 1-6000. Provide a screenshot similar to the one below that shows your command and results. You will note that 3 new ports have been exposed.
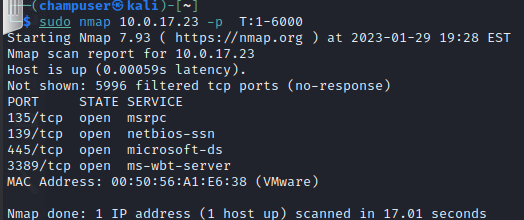
nmap command:
sudo nmap 10.0.17.23 -p T:1-6000Deliverable 8. Figure out how to run a version scan against only the ports exposed above. Provide a screenshot showing your nmap command and the output similar to the one below.
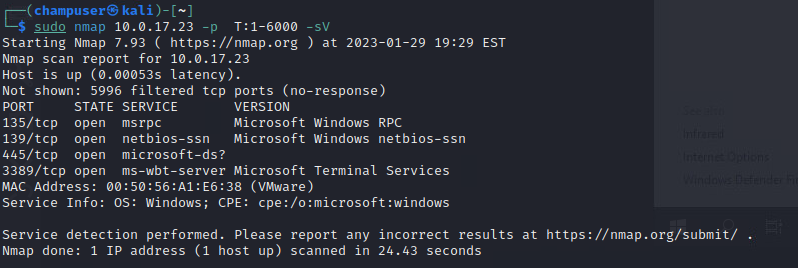
nmap command:
sudo nmap 10.0.17.23 -p T:1-6000 -sVDeliverable 9. Increase the output by running OS Detection, Version Detection, Script Scanning and traceroute against your windows 10 target. Provide a screenshot showing your command and output similar to the one below. You will notice we have smb and netbios related information.
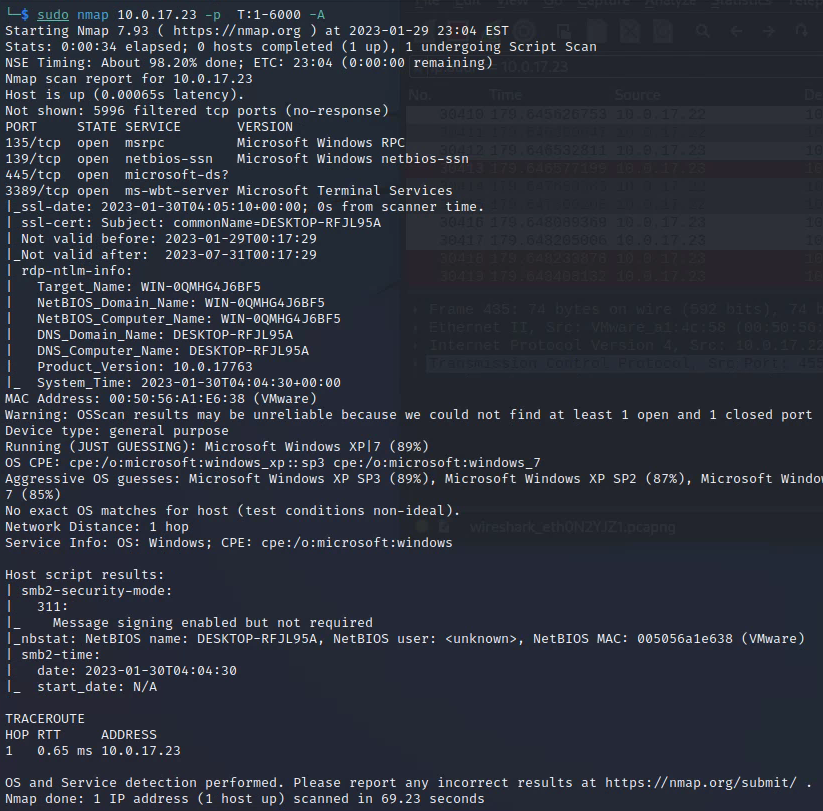
nmap command:
sudo nmap 10.0.17.23 -p T:1-6000 -A