Lab 6.1: Cracking Linux Passwords with JtR and Hashcat
Summary
During this lab we explored John the Ripper, Hashcat, and more understanding of the shadow file.
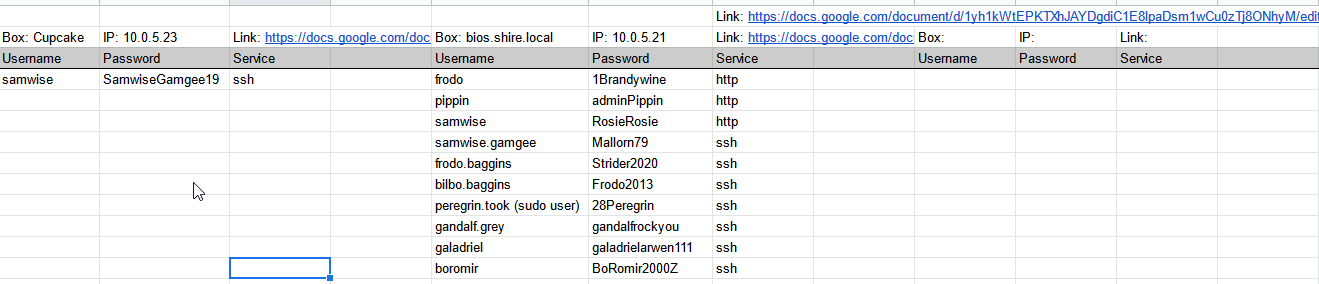
Deliverable 1. Provide screenshots similar to the ones above showing the last 3 entries in /etc/passwd and /etc/shadow.
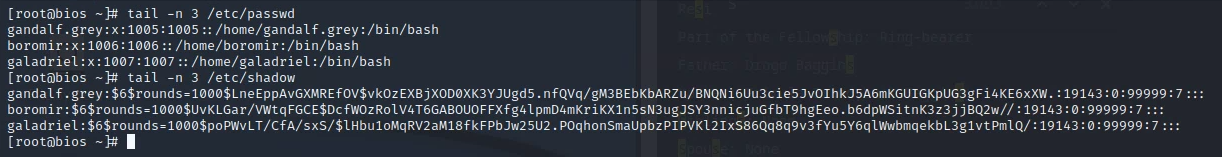
Deliverable 2. Research what hashing algorithm is being used on this server, one of the fields in /etc/shadow points to the format. Explain this.
$6$ - SHA-512
$rounds=1000$ - “The more rounds are performed the higher the CPU requirements are. This is a safety mechanism which might help counter brute-force attacks in the face of increasing computing power.” https://access.redhat.com/articles/1519843
$LneEppAvGXMREfOV$ - Salt
$kOzEXBjXOD0XK3YJUgd5.nfQVq/gM3BEbKbARZu/BNQNi6Uu3cie5JvOIhkJ5A6mKGUIGKpUG3gFi4KE6xXW.$ - Salt + User password
Deliverable 3. Examine user Galadriel’s shadow entry.
- What is the salt?
- LneEppAvGXMREfOV
- What is the hashed salt+password?
- kOzEXBjXOD0XK3YJUgd5.nfQVq/gM3BEbKbARZu/BNQNi6Uu3cie5JvOIhkJ5A6mKGUIGKpUG3gFi4KE6xXW.
Provide a screenshot that shows each explicitly labeled. Note, you may see a different format between password hashes. Some explicitly indicate the number of “rounds”.
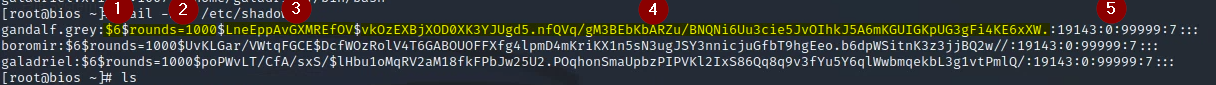
1 = Algorithm
2 = Number of rounds
3 = Salt
4 = Salt + Passwd
5 = Extra information Devin said was rarely used…
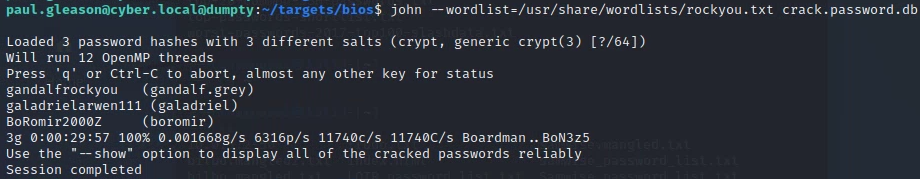
Deliverable 4. Figure out how to use the unshadow utility to create a file usable by John the Ripper(JtR) and then crack the unshadowed files hashes using JtR. Provide a screenshot showing your results.
https://www.cyberciti.biz/faq/unix-linux-password-cracking-john-the-ripper/
Cracking Passwords in a Virtual Machine can be an exercise in frustration. Generally, the performance of john and hashcat are abysmal. The following link describes how to leverage humpty.cyber.local to run your cracks on a decent physical workstation.
Deliverable 5. Let’s see if you can reverse engineer the shadow file using python. We will use peregrin.took’s bios hash.
The grayed out area has the plaintext password for gandalf. Provide a screenshot similar to the one below. Use Boromir or Galadriel’s shadow entry.
Deliverable 6. crack at least one of the hashes using hashcat and show the result in a screenshot similar to the one below (hit s for status). Again, consider leveraging humpty or your own physical system for this crack.
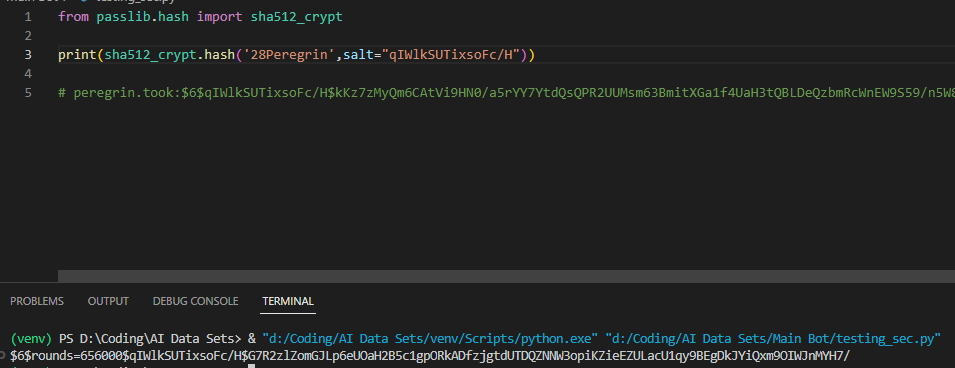
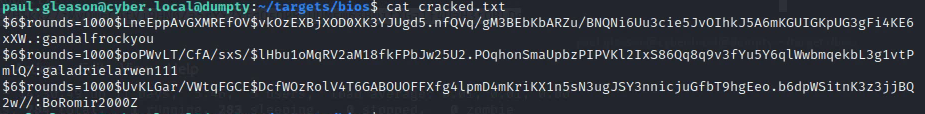
Deliverable 7. Start a text or csv or markdown file similar to the one below. Include your successful guesses from Week 5 as well as the cracks from this week. We will need this data in our future adventures. a listing or screenshot of all your acquired passwords. This type of material is normally called “loot” in hacker parlance. Documenting uncracked hashes is also a great idea. You may have better luck cracking them as you learn more about your target or decide to crack on a real workstation instead of a kali vm.