Lab 2.2: Syslog Organization on log01
Summary:
During this lab we setup mgtm01 and setup the fw to allow connection to the 172.16.150.0/24 network. Then setup chrome remote desktop on mgmt01, ssh key authnetication from mgmt01 to log01. Then setup authpriv messages for rsyslog from web01 and vyos.
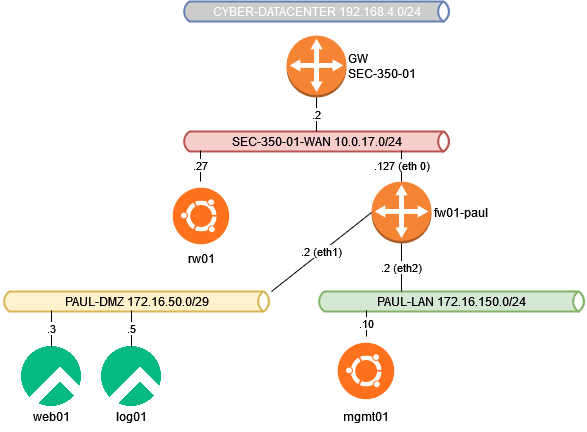
Network Diagram:
Vyos Password Change:
I actually did this during our first lab because I thought it was a gotcha. VYOS Change User passwd
SSH keybased authentication:
ssh-keygen
ssh-copy-id <user>@<ip>Authpriv Messages on Linux Systems:
Server
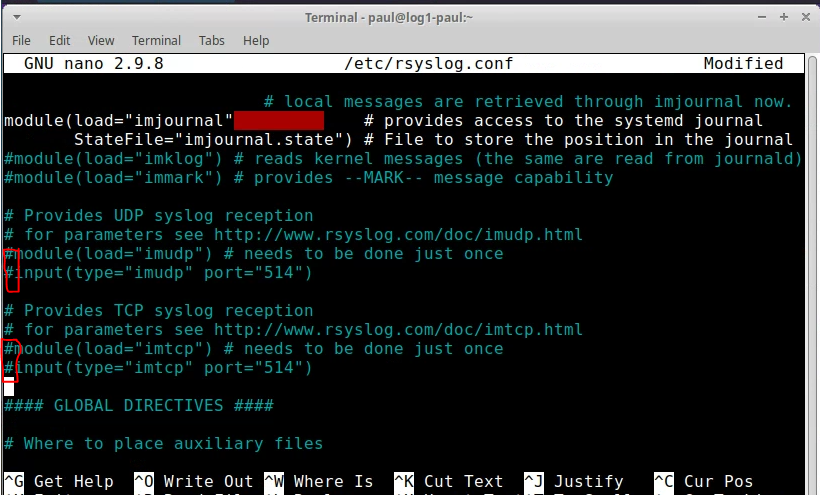
Modify the /etc/rsyslog.conf
- Comment out those 4 lines
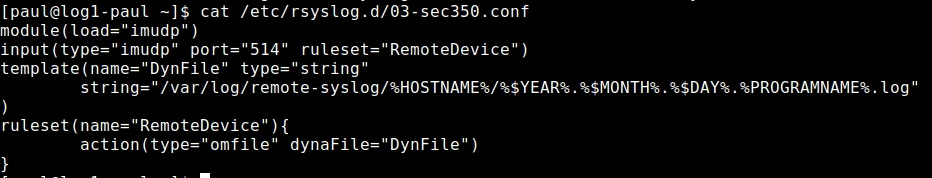
Add Custom config to /etc/rsyslog.d/<config_name>.conf
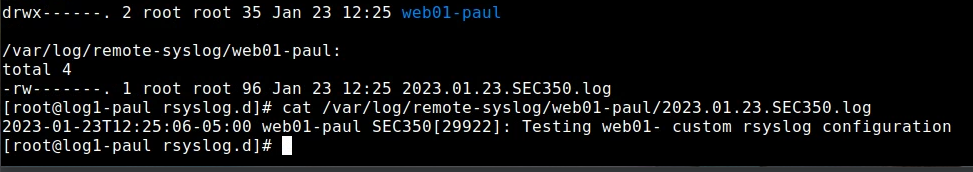
With this config logs will now be output like:
Client:
Edit the rsyslog.d/ config
sudo nano /etc/rsyslog.d/sec350-client.conf- Add this line (IP is log machine)
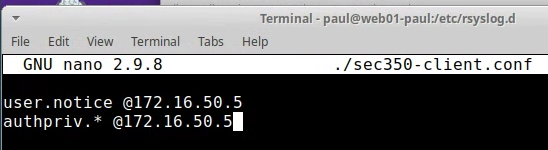
Restart rsyslog.service
sudo systemctl restart rsyslog.serviceForward Authentication events from vyos:
Configure
Set system syslog host <log-ip> facility authpriv level info
Commit
SaveNotes and Difficulties:
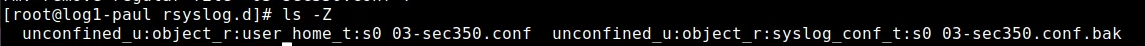
SE linux got me once again… I had scp’d to the user home dir the 03-sec250.conf file to log1 and then mv’d it to /etc/rsyslog.d/. This made it so the file had kept the user_home_t tag seen below
Fix:
cat <file> > <file>.bak
rm <file>
mv <file>.bak <file>This will make a new file and remove the user_home_t tag and allow SE linux to use the config file.
VYOS Config:
set interfaces ethernet eth0 address '10.0.17.127/24'
set interfaces ethernet eth0 description 'SEC350-WAN'
set interfaces ethernet eth1 address '172.16.50.2/29'
set interfaces ethernet eth1 description 'PAUL-DMZ'
set interfaces ethernet eth2 address '172.16.150.2/24'
set interfaces ethernet eth2 description 'PAUL-LAN'
set nat source rule 10 description 'NAT FROM DMZ to WAN'
set nat source rule 10 outbound-interface 'eth0'
set nat source rule 10 source address '172.16.50.0/29'
set nat source rule 10 translation address 'masquerade'
set nat source rule 20 description 'NAT FROM LAN to WAN'
set nat source rule 20 outbound-interface 'eth0'
set nat source rule 20 source address '172.16.150.0/24'
set nat source rule 20 translation address 'masquerade'
set protocols static route 0.0.0.0/0 next-hop 10.0.17.2
set service dns forwarding allow-from '172.16.50.0/29'
set service dns forwarding allow-from '172.16.150.0/24'
set service dns forwarding listen-address '172.16.50.2'
set service dns forwarding listen-address '172.16.150.2'
set service dns forwarding system
set service ssh listen-address '0.0.0.0'
set system host-name 'fw1-paul'
set system name-server '10.0.17.2'