Lab 1.1: Routing and DMZ (VYOS/LOG)
Summary
During this lab we started to configure fw01, log01, rw01, web01.
VYOS
Version Control:
To change VYOS rules and save:
configure
<Enter Commands>
commit
savehostname:
set system host-name <HOSTNAME>interfaces:
Description:
set interfaces ethernet <ADAPTER> description <DESCRIPTION>Set IP:
set interfaces ethernet <ADAPTER> address <IP ADDRESS>/<SUBNET>gateway/route:
Command below will route all traffic to the gateway ip:
set protocols static route 0.0.0.0/0 next-hop <GATEWAY>dns:
set system name-server <NAME SERVER IP>nat:
set nat source rule 10 description <DESCRIPTION>
set nat source rule 10 outbound-interface <ADAPTER>
set nat source rule 10 source address <IP OR NETWORK>/<SUBNET>
set nat source rule 10 translation address masqueradedns forwarding:
Below allows listening address to reslove requests from the allowed IP or Network
set service dns forwarding listen-address <LISTENING IP>
set service dns forwarding allow-from <IP OR NETWORK>/<SUBNET>
set service dns forwarding systemSYSLOG
Server
- Install syslog
sudo yum install rsyslog- Allow 514 tcp and udp. Example below if for firewalld systems
firewall-cmd --permanent --zone=public --add-port=514/tcp
firewall-cmd --permanent --zone=public --add-port=514/udp
firewall-cmd --reload- Now configure the rsyslog.conf
sudo vi /etc/rsyslog.conf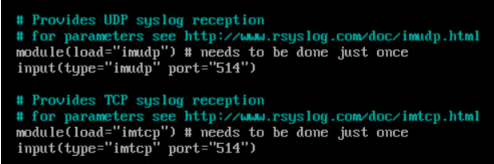
- Restart and enable rsyslog.service
sudo systemctl restart rsyslog.service
sudo systemctl enable rsyslog.service- Once you setup the client you will be able to see the client test with:
sudo tail -f /var/log/messagesClient
- Install syslog
sudo yum install rsyslog- Allow 514 tcp and udp. Example below if for firewalld systems
firewall-cmd --permanent --zone=public --add-port=514/tcp
firewall-cmd --permanent --zone=public --add-port=514/udp
firewall-cmd --reload- Make/edit the file
/etc/rsyslog.d/sec350.conf
sudo vi /etc/rsyslog.d/sec350.conf- Add the line
user.notice @<IP OF LOG Machine>- To test the logger:
logger -t test TESTTOLOG- Now do step 5 of server and it should show a message like this:
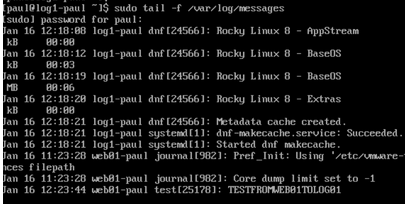
Notes
VYOS Config after this lab:
set interfaces ethernet eth0 address '10.0.17.127/24'
set interfaces ethernet eth0 description 'SEC350-WAN'
set interfaces ethernet eth1 address '172.16.50.2/29'
set interfaces ethernet eth1 description 'PAUL-DMZ'
set interfaces ethernet eth2 address '172.16.150.2/24'
set interfaces ethernet eth2 description 'PAUL-LAN'
set nat source rule 10 description 'NAT FROM DMZ to WAN'
set nat source rule 10 outbound-interface 'eth0'
set nat source rule 10 source address '172.16.50.0/29'
set nat source rule 10 translation address 'masquerade'
set protocols static route 0.0.0.0/0 next-hop 10.0.17.2
set service dns forwarding allow-from '172.16.50.0/29'
set service dns forwarding listen-address '172.16.50.2'
set service dns forwarding system
set service ssh listen-address '0.0.0.0'
set system host-name 'fw1-paul'
set system name-server '10.0.17.2'VYOS Change User passwd:
https://support.vyos.io/en/kb/articles/set-change-the-password-of-a-user
set system login user vyos authentication plaintext-password