Lab 10.1: Linux - Permission Vulnerabilities
suid Programs
#include <stdlib.h>
#include <pwd.h>
#include <stdio.h>
#include <unistd.h>
/*
SEC335 Illustrate SUID Programs
* based on: https://stackoverflow.com/questions/8953424/how-to-get-the-username-in-c-c-in-linux
* Make sure run the following
* sudo chown root:root nameofprogram
* sudo chmod u+s nameofprogram
*/
int main(int argc, char *argv[])
{
struct passwd *pw;
uid_t uid;
uid = geteuid ();
pw = getpwuid (uid);
if (pw)
{
puts (pw->pw_name);
exit (EXIT_SUCCESS);
}
else
{
puts ("Error");
exit (EXIT_FAILURE);
}
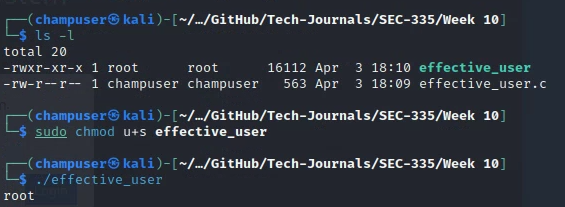
}Deliverable 1. Using the code above, create a file called effective user.c and compile and execute the file as a normal user and using sudo. Provide a screenshot similar to the one below.
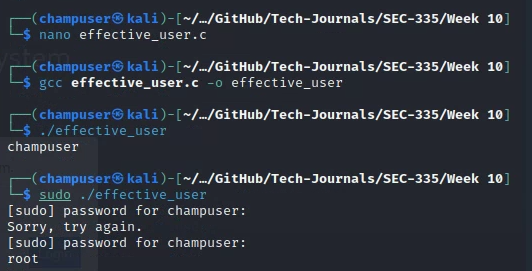
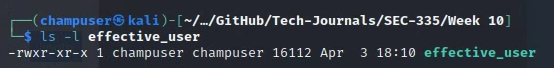
Deliverable 2. What are the octal (numeric) permissions of the effective user program? Using ls -l you should be able to calculate these permissions, you can also use the “stat” program as a shortcut. Remember r=4,w=2, x=1, and ”-” is a 0
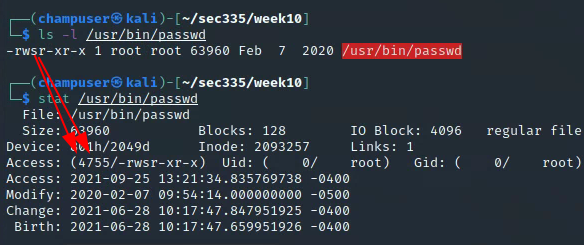
Repeat the following use of ls -l and stat on the passwd program
Deliverable 3. Figure out how to change the ownership of your c program executable such that the file is owned by user: root and group: root. Once you’ve done that, add the suid bit to the program (this is shown in the screenshot) and execute the program as a normal user. Provide a screenshot similar to the one below:
Deliverable 4. Hit the internet and find a means to search for suid programs across your kali system. Do so as a normal user as this is a privilege escalation technique you might use. Make sure to document this. You will need to deal with permissions errors by piping those to /dev/null. Provide a screenshot showing your command and listing similar to that below. Your own sudo program should be in the list.
find / -perm -4000 2>/dev/null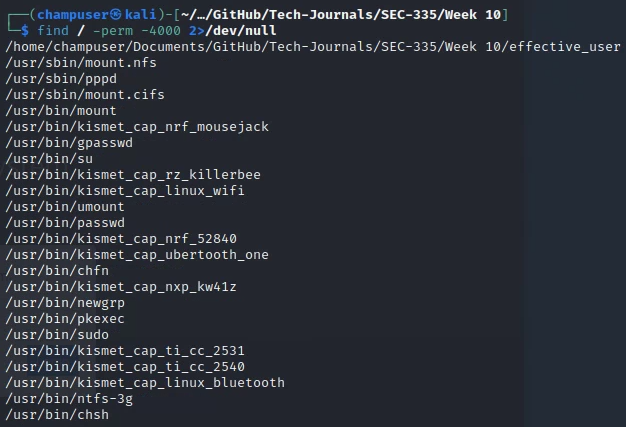
Deliverable 5. A suid program has been hidden on rocky (10.0.17.200). Please hunt it down. Provide a screenshot that shows the command and file found. It will be obvious and the name will start with a ‘b’.
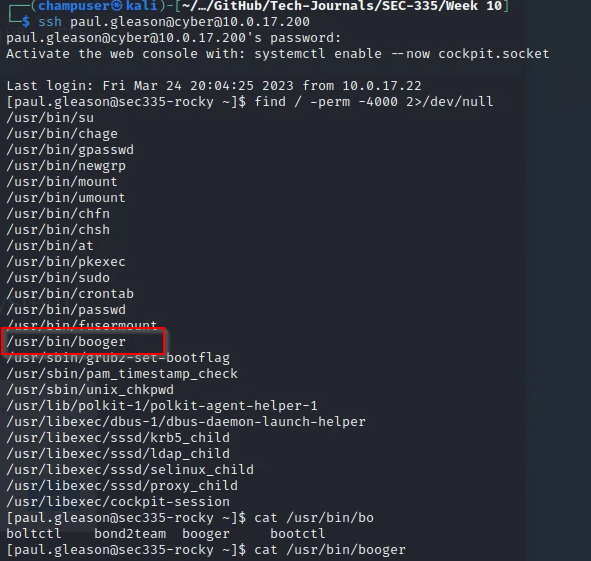
rwx errors
Deliverable 6. Consider the following screenshot. This user created a file under /etc/ that is world writable. Were this file to be of any security relevance, this could be a problem. Create such a file, and figure out how to find it. Show your command.
find /etc -type f -perm /o+w 2>/dev/null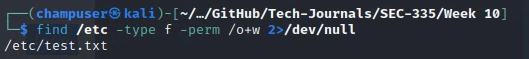
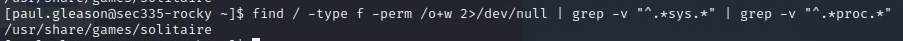
Deliverable 7. A world writable file has been hidden on rocky. Please hunt it down. Provide a screenshot that shows the command and file found. It will start with an ‘s’. (note, the sys and proc directories will give you a lot of false positives)
find / -type f -perm /o+w 2>/dev/null | grep -v "^.*sys.*" | grep -v "^.*proc.*"