Assessment Prep
Network
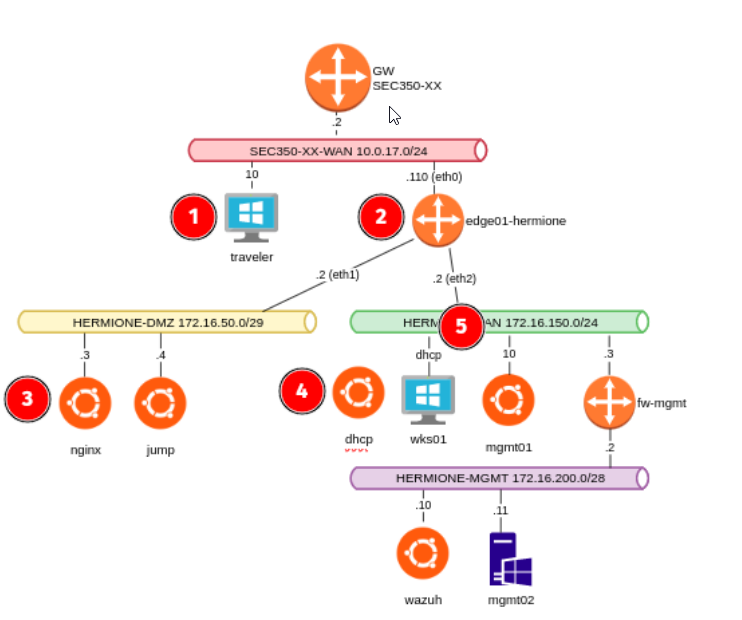
Edge01-Paul (10.0.17.127/24, 172.16.50.2/29, 172.16.150.2/24)
Wiring
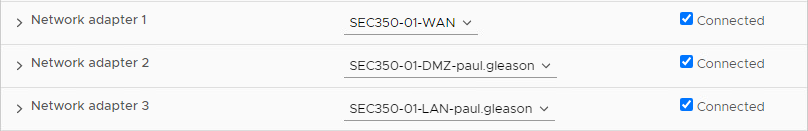
Main Setup
set service ssh listen-address '0.0.0.0'
set interfaces ethernet eth0 address '10.0.17.127/24'Pull down config on Traveler
wget -O vyos_config "https://raw.githubusercontent.com/ChampPG/Tech-Journals/main/SEC-350/Assessment%20Prep/vyos_config"
scp vyos_config vyos@10.0.17.127:Load Config
configure
load vyos_config
commit
saveSSH, Hostname, Route, and Server name
set system host-name 'edge01-paul'
set system name-server '10.0.17.2'
set protocols static route 0.0.0.0/0 next-hop 10.0.17.2
set service ssh listen-address '0.0.0.0'
set system login user vyos authentication plaintext-password <Password>
# Leave out this line till the end...
del service ssh listen-address '0.0.0.0'
set service ssh listen-address '172.16.150.2'Set Interfaces
set interfaces ethernet eth0 address '10.0.17.127/24'
set interfaces ethernet eth0 description 'SEC350-WAN'
set interfaces ethernet eth1 address '172.16.50.2/29'
set interfaces ethernet eth1 description 'PAUL-DMZ'
set interfaces ethernet eth2 address '172.16.150.2/24'
set interfaces ethernet eth2 description 'PAUL-LAN'set zone-policy zone DMZ from LAN firewall name 'LAN-to-DMZ'
set zone-policy zone DMZ from WAN firewall name 'WAN-to-DMZ'
set zone-policy zone DMZ interface 'eth1'
set zone-policy zone LAN from DMZ firewall name 'DMZ-to-LAN'
set zone-policy zone LAN from WAN firewall name 'WAN-to-LAN'
set zone-policy zone LAN interface 'eth2'
set zone-policy zone WAN from DMZ firewall name 'DMZ-to-WAN'
set zone-policy zone WAN from LAN firewall name 'LAN-to-WAN'
set zone-policy zone WAN interface 'eth0'DNS
set service dns forwarding allow-from '172.16.150.0/24'
set service dns forwarding listen-address '172.16.50.2'
set service dns forwarding listen-address '172.16.150.2'
set service dns forwarding system
set service dns forwarding allow-from '172.16.50.0/29'RIP
set protocols rip interface eth2
set protocols rip network '172.16.50.0/29'NAT Rules
NAT Source from DMZ to WAN
set nat source rule 10 description 'NAT FROM DMZ to WAN'
set nat source rule 10 outbound-interface 'eth0'
set nat source rule 10 source address '172.16.50.0/29'
set nat source rule 10 translation address 'masquerade'NAT from MGMT to WAN
set nat source rule 30 description 'NAT FROM MGMT to WAN'
set nat source rule 30 outbound-interface 'eth0'
set nat source rule 30 source address '172.16.200.0/28'
set nat source rule 30 translation address 'masquerade'NAT Source from LAN to WAN
set nat source rule 20 description 'NAT FROM LAN to WAN'
set nat source rule 20 outbound-interface 'eth0'
set nat source rule 20 source address '172.16.150.0/24'
set nat source rule 20 translation address 'masquerade'NAT Destination from WAN HTTP to NGINX
set nat destination rule 10 description 'WAN HTTP to NGINX'
set nat destination rule 10 destination port '80'
set nat destination rule 10 inbound-interface 'eth0'
set nat destination rule 10 protocol 'tcp'
set nat destination rule 10 translation address '172.16.50.3'
set nat destination rule 10 translation port '80'NAT Destination from WAN to Jump
set nat destination rule 20 description 'WAN to JUMP'
set nat destination rule 20 destination port '22'
set nat destination rule 20 inbound-interface 'eth0'
set nat destination rule 20 protocol 'tcp'
set nat destination rule 20 translation address '172.16.50.4'
set nat destination rule 20 translation port '22'Firewall Rules
DMZ-to-LAN
set firewall name DMZ-to-LAN default-action 'drop'
set firewall name DMZ-to-LAN enable-default-log
ash
set firewall name DMZ-to-LAN rule 1 action 'accept'
set firewall name DMZ-to-LAN rule 1 state established 'enable'
set firewall name DMZ-to-LAN rule 10 action 'accept'
set firewall name DMZ-to-LAN rule 10 description 'wazuh agent communications with wazuh server'
set firewall name DMZ-to-LAN rule 10 destination address '172.16.200.10'
set firewall name DMZ-to-LAN rule 10 destination port '1514-1515'
set firewall name DMZ-to-LAN rule 10 protocol 'tcp'DMZ-to-WAN
set firewall name DMZ-to-WAN default-action 'drop'
set firewall name DMZ-to-WAN enable-default-log
set firewall name DMZ-to-WAN rule 1 action 'accept'
set firewall name DMZ-to-WAN rule 1 state established 'enable'
# Only use line below if NGINX needs network
set firewall name DMZ-to-WAN rule 999 action 'accept'
set firewall name DMZ-to-WAN rule 999 source address '172.16.50.3'LAN-to-DMZ
set firewall name LAN-to-DMZ default-action 'drop'
set firewall name LAN-to-DMZ enable-default-log
set firewall name LAN-to-DMZ rule 1 action 'accept'
set firewall name LAN-to-DMZ rule 1 state established 'enable'
set firewall name LAN-to-DMZ rule 10 action 'accept'
set firewall name LAN-to-DMZ rule 10 description 'Allow HTTP from LAN to NGINX'
set firewall name LAN-to-DMZ rule 10 destination address '172.16.50.3'
set firewall name LAN-to-DMZ rule 10 destination port '80'
set firewall name LAN-to-DMZ rule 10 protocol 'tcp'
set firewall name LAN-to-DMZ rule 20 action 'accept'
set firewall name LAN-to-DMZ rule 20 description 'ssh from mgmt01 to DMZ'
set firewall name LAN-to-DMZ rule 20 destination address '172.16.50.0/29'
set firewall name LAN-to-DMZ rule 20 destination port '22'
set firewall name LAN-to-DMZ rule 20 protocol 'tcp'
set firewall name LAN-to-DMZ rule 20 source address '172.16.150.10'LAN-to-WAN
set firewall name LAN-to-WAN default-action 'drop'
set firewall name LAN-to-WAN enable-default-log
set firewall name LAN-to-WAN rule 1 action 'accept'WAN-to-LAN
set firewall name WAN-to-LAN default-action 'drop'
set firewall name WAN-to-LAN enable-default-log
set firewall name WAN-to-LAN rule 1 action 'accept'
set firewall name WAN-to-LAN rule 1 state established 'enable'WAN-to-DMZ
set firewall name WAN-to-DMZ default-action 'drop'
set firewall name WAN-to-DMZ enable-default-log
set firewall name WAN-to-DMZ rule 1 action 'accept'
set firewall name WAN-to-DMZ rule 1 state established 'enable'
set firewall name WAN-to-DMZ rule 10 action 'accept'
set firewall name WAN-to-DMZ rule 10 description 'Allow HTTP from WAN to DMZ'
set firewall name WAN-to-DMZ rule 10 destination address '172.16.50.3'
set firewall name WAN-to-DMZ rule 10 destination port '80'
set firewall name WAN-to-DMZ rule 10 protocol 'tcp'
set firewall name WAN-to-DMZ rule 20 action 'accept'
set firewall name WAN-to-DMZ rule 20 description 'Allow SSH from WAN to DMZ'
set firewall name WAN-to-DMZ rule 20 destination address '172.16.50.4'
set firewall name WAN-to-DMZ rule 20 destination port '22'
set firewall name WAN-to-DMZ rule 20 protocol 'tcp'Traveler (10.0.17.27/24)
User Config/Hostname:
$Password = Read-Host -AsSecureString
New-LocalUser "paul" -Password $Password -FullName "paul" -Description "Hello me"
Add-LocalGroupMember -Group "Administrators" -Member "paul"
Rename-Computer -NewName "traveler-paul" -RestartNetwork Config:
#SET Network
# look at what the ifIndex is
Get-Netadapter
New-NetIPAddress -InterfaceIndex <IfIndex> -IPAddress 10.0.17.27 -PrefixLength 24 -DefaultGateway 10.0.17.2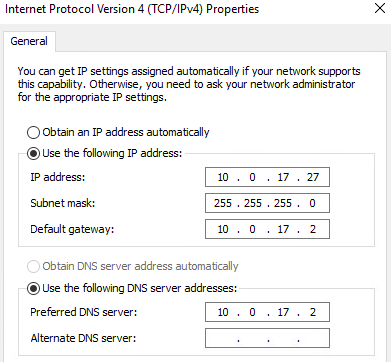
Run as Admin:
# Install OpenSSH , does not install if "ssh" folder exists
if (!(Test-Path "C:\ProgramData\ssh\ssh_host_rsa_key")) {
Add-WindowsCapability -Online -Name OpenSSH.Server~~~~0.0.1.0
}
# Start now and on startup
Start-Service sshd
Set-Service -Name sshd -StartupType AutomaticRun as User:
# Generate Keys
ssh-keygen.exe -f .\ssh-keys MGMT pass keys to jump
#!/bin/bash
WINDOWSUSER="paul"
WINDOWSIP="10.0.17.27"
JUMPUSER="paul-jump"
JUMPIP="172.16.50.4"
sftp $WINDOWSUSER@$WINDOWSIP:ssh-keys.pub
scp ssh-keys.pub paul@$JUMPIP:travel.pub
ssh paul@$JUMPIP <<END
sudo -i
cat /home/paul/travel.pub >> /home/$JUMPUSER/.ssh/authorized_keys
ENDNGINX (172.16.50.3/29)
User and Hostname Setup:
sudo adduser paul
sudo usermod -aG sudo paul
sudo hostnamectl set-hostname nginx-paul
sudo reboot
sudo deluser champuserNetwork Setup:
#Set Networking
# If nmtui
nmtui
#Address = 172.16.50.3
#Gateway = 172.16.50.2
#DNS Server = 172.16.50.2
# If Netplan
/bin/cat << EOM >/etc/netplan/00-installer-config.yaml
network:
ethernets:
<adapter>:
addresses: [172.16.50.3/29]
gateway4: 172.16.50.2
namerservers:
addresses: [172.16.50.2]
version: 2
EOM
sudo netplan tryNginx Service Setup:
sudo apt update
sudo apt install nginx -y
cd /var/www/html
touch index.html
/bin/cat << EOM >index.html
Paul Gleason nginx
EOM
sudo systemctl enable nginx
sudo systemctl start nginx
sudo systemctl status nginxWazuh Agent Setup:
MGMT
scp wazuh-agent-4.3.10.deb paul@172.16.50.3:On NGINX
sudo WAZUH_MAsudo WAZUH_MANAGER='172.16.200.10' WAZUH_AGENT_GROUP='linux' dpkg -i ./wazuh-agent-4.3.10.deb
sudo systemctl daemon-reload
sudo systemctl enable wazuh-agent
sudo systemctl start wazuh-agentDHCP (172.16.150.5/24)
User and Hostname Setup:
sudo adduser paul
sudo usermod -aG sudo paul
sudo hostnamectl set-hostname dhcp-paul
sudo reboot
sudo deluser champuserNetwork Setup:
Warning
The netplan config is out of date please following the link to the new way to format a netplan config
#Set Networking
# If nmtui
nmtui
#Address = 172.16.150.5
#Gateway = 172.16.150.2
#DNS Server = 172.16.150.2
# If Netplan
/bin/cat << EOM >/etc/netplan/00-installer-config.yaml
network:
ethernets:
<adapter>:
addresses: [172.16.150.5/24]
gateway4: 172.16.150.2
namerservers:
addresses: [172.16.150.2]
version: 2
EOM
sudo netplan generate && sudo netplan tryDHCP Setup:
sudo apt update
sudo apt install isc-dhcp-server -y
cp /etc/dhcp/dhcpd.conf /etc/dhcp/dhcpd.conf.backup
FILE="/etc/dhcp/dhcpd.conf"
/bin/cat << EOM >$FILE
subnet 172.16.150.0 netmask 255.255.255.0 {
option routers 172.16.150.2;
option subnet-mask 255.255.255.0;
option domain-name-servers 172.16.150.2;
range 172.16.150.100 172.16.150.150;
default-lease-time 3600;
max-lease-time 14400;
}
EOM
systemctl enable isc-dhcp-server
systemctl start isc-dhcp-server
systemctl status isc-dhcp-serverWazuh Agent Setup:
MGMT
scp wazuh-agent-4.3.10.deb paul@172.16.150.5:On NGINX
sudo WAZUH_MAsudo WAZUH_MANAGER='172.16.200.10' WAZUH_AGENT_GROUP='linux' dpkg -i ./wazuh-agent-4.3.10.deb
sudo systemctl daemon-reload
sudo systemctl enable wazuh-agent
sudo systemctl start wazuh-agent