VPN Project
Steps
Edge Firewall Rules
set firewall name WAN-to-DMZ rule 30 action 'accept'
set firewall name WAN-to-DMZ rule 30 description 'Port Forward Wireguard from jump'
set firewall name WAN-to-DMZ rule 30 destination address '172.16.50.4'
set firewall name WAN-to-DMZ rule 30 destination port '51820'
set firewall name WAN-to-DMZ rule 30 protocol 'udp'
set nat destination rule 30 destination port 51820
set nat destination rule 30 inbound-interface eth0
set nat destination rule 30 protocol udp
set nat destination rule 30 translation address 172.16.50.4
set nat destination rule 30 translation port 51820
set nat destination rule 30 description 'Port Forward Wireguard from jump'Rule 999 to allow jump to talk with the internet
set firewall name DMZ-to-WAN rule 999 action accept
set firewall name DMZ-to-WAN rule 999 source address 172.16.50.4Note: delete this after the script is run
Script usage
Download script:
wget https://raw.githubusercontent.com/ChampPG/Tech-Journals/main/SEC-350/Project%20Remote/wireguard-setup.shScript:
#!/bin/bash
# Sources:
# https://www.wireguard.com/quickstart/
# https://askubuntu.com/questions/906325/ubuntu-iptables-nat-router-port-forwarding
# https://superuser.com/questions/269980/iptables-for-transparent-tcp-proxy
# Prompt user to enter the name of their main Ethernet adapter
read -p "Enter the name of your main Ethernet adapter: " adapter_name
# Install WireGuard
sudo apt update
sudo apt install wireguard -y
sudo umask 077
sudo mkdir -p /etc/wireguard/
# Keygen
sudo wg genkey | sudo tee /etc/wireguard/privatekey-server | wg pubkey | sudo tee /etc/wireguard/publickey-server
sudo wg genkey | sudo tee /etc/wireguard/privatekey-client | wg pubkey | sudo tee /etc/wireguard/publickey-client
# Generate server configuration file
sudo touch /etc/wireguard/wg0.conf
sudo chmod 600 /etc/wireguard/wg0.conf
sudo tee -a /etc/wireguard/wg0.conf << END
[Interface]
Address = 10.0.0.1/24
SaveConfig = true
PrivateKey = $(sudo cat /etc/wireguard/privatekey-server)
ListenPort = 51820
PreUp = sysctl -w net.ipv4.ip_forward=1
PreUp = iptables -t nat -A PREROUTING -p tcp -d 10.0.0.1 --dport 3389 -j DNAT --to-destination 172.16.200.11:3389
PreUp = iptables -t nat -A POSTROUTING -o $adapter_name -j MASQUERADE
PostDown = iptables -t nat -D POSTROUTING -o $adapter_name -j MASQUERADE
PostDown = iptables -t nat -D PREROUTING -p tcp -d 10.0.0.1 --dport 3389 -j DNAT --to-destination 172.16.200.11:3389
[Peer]
PublicKey = $(sudo cat /etc/wireguard/publickey-client)
AllowedIPs = 10.0.0.2/32
PersistentKeepalive = 21
END
# Generate client configuration file
sudo mkdir -p /etc/wireguard/clients/
sudo tee /etc/wireguard/clients/client1-GCorp.conf << END
[Interface]
Address = 10.0.0.2/24
PrivateKey = $(sudo cat /etc/wireguard/privatekey-client)
[Peer]
PublicKey = $(sudo cat /etc/wireguard/publickey-server)
Endpoint = 10.0.17.127:51820
AllowedIPs = 0.0.0.0/0
PersistentKeepalive = 21
END
# Restart WireGuard service
sudo systemctl restart wg-quick@wg0.serviceNote: You will need to change the endpoint to contain your public ip
Make Script Executable:
chmod +x ./wireguard-setup.shNote: Before running the script take not of which ethernet adapter you want to use. As you can see below mine is ens160.
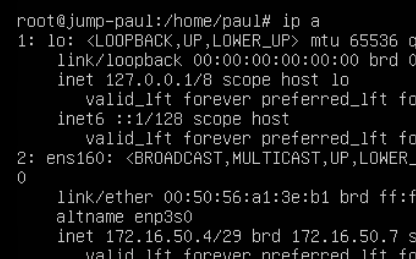
Run the script:
You will be prompted for the adapter just put it in as it reads in the `ip a` for example mine was ens160 so I would just put ens160.
./wireguard-setup.shOnce the script is done you will have a client config and the wg0.conf. We want to get that client config over to the client.
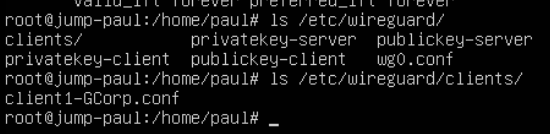
Client Setup:
I just use the msi install: https://download.wireguard.com/windows-client/
Now once you have the client config on the client machine.
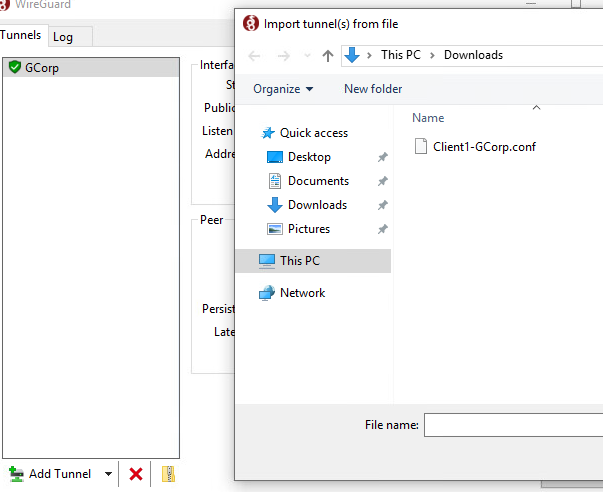
Now open wiregaurd and press `Add Tunnel` in the bottom left. Then navigate the your client config.
Note: If you see Latest Handshake then you have an active connection to the server. For an extra test you can ping the gateway IP of your vpn network.